Cyber Security Breaches Survey 2022
Updated 11 July 2022
Overview
The Cyber Security Breaches Survey is an influential research study for UK cyber resilience, aligning with the National Cyber Strategy. It is primarily used to inform government policy on cyber security, making the UK cyber space a secure place to do business. The study explores the policies, processes, and approaches to cyber security for businesses, charities, and educational institutions. It also considers the different cyber attacks these organisations face, as well as how these organisations are impacted and respond.
For this latest release, the quantitative survey was carried out in winter 2021/22 and the qualitative element in early 2022.
Responsible analyst: Maddy Ell
Responsible statistician: Robbie Gallucci
Statistical enquiries: evidence@dcms.gov.uk
General enquiries: enquiries@dcms.gov.uk
Media enquiries: 020 7211 2210
Key findings
Cyber attacks
Our survey results show that in the last 12 months, 39% of UK businesses identified a cyber attack, remaining consistent with previous years of the survey. However, we also find that enhanced cyber security leads to higher identification of attacks, suggesting that less cyber mature organisations in this space may be underreporting.
Table 1.1: Proportion of UK businesses identifying cyber attacks each year
| 2017 | 2018 | 2019 | 2020 | 2021 | 2022 |
|---|---|---|---|---|---|
| 46% | 43% | 32% | 46% | 39% | 39% |
Attack type
Of the 39% of UK businesses who identified an attack, the most common threat vector was phishing attempts (83%). Of the 39%, around one in five (21%) identified a more sophisticated attack type such as a denial of service, malware, or ransomware attack. Despite its low prevalence, organisations cited ransomware as a major threat, with 56% of businesses having a policy not to pay ransoms.
Frequency & impact
Within the group of organisations reporting cyber attacks, 31% of businesses and 26% of charities estimate they were attacked at least once a week. One in five businesses (20%) and charities (19%) say they experienced a negative outcome as a direct consequence of a cyber attack, while one third of businesses (35%) and almost four in ten charities (38%) experienced at least one negative impact.
Cost of attacks
Looking at organisations reporting a material outcome, such as loss of money or data, gives an average estimated cost of all cyber attacks in the last 12 months of £4,200. Considering only medium and large businesses; the figure rises to £19,400. We acknowledge the lack of framework for financial impacts of cyber attacks may lead to underreporting.
Cyber hygiene
The government guidance ‘10 Steps to Cyber Security’ breaks down the task of protecting an organisation into 10 key components. The survey finds 49% of businesses and 39% of charities[footnote 11] have acted in at least five of these 10 areas. In particular, access management surveyed most favourably, while supply chain security was the least favourable.
Board engagement
Around four in five (82%) of boards or senior management within UK businesses rate cyber security as a ‘very high’ or ‘fairly high’ priority, an increase on 77% in 2021. 72% in charities rate cyber security as a ‘very high’ or ‘fairly high’ priority. Additionally, 50% of businesses and 42% of charities say they update the board on cyber security matters at least quarterly.
Size differential
Larger organisations are correlated throughout the survey with enhanced cyber security, likely as a consequence of increased funding and expertise. For large businesses’ cyber security; 80% update the board at least quarterly, 63% conducted a risk assessment, and 61% carried out staff training; compared with 50%, 33% and 17% respectively for all businesses.
Risk management
Just over half of businesses (54%) have acted in the past 12 months to identify cyber security risks, including a range of actions, where security monitoring tools (35%) were the most common. Qualitative interviews however found that limited board understanding meant the risk was often passed on to; outsourced cyber providers, insurance companies, or an internal cyber colleague.
Table 1.2: Proportion of UK businesses acting to identify cyber risks each year
| 2017 | 2018 | 2019 | 2020 | 2021 | 2022 |
|---|---|---|---|---|---|
| 57% | 56% | 62% | 64% | 52% | 54% |
Outsourcing & supply chain
Small, medium, and large businesses outsource their IT and cyber security to an external supplier 58%, 55%, and 60% of the time respectively, with organisations citing access to greater expertise, resources, and standard for cyber security. Consequently, only 13% of businesses assessed the risks posed by their immediate suppliers, with organisations saying that cyber security was not an important factor in the procurement process.
Incident management
Incident management policy is limited with only 19% of businesses having a formal incident response plan, while 39% have assigned roles should an incident occur. In contrast, businesses show a clear reactive approach when breaches occur, with 84% of businesses saying they would inform the board, while 73% would make an assessment of the attack.
External engagement
Outside of working with external cyber security providers, organisations most keenly engage with insurers, where 43% of businesses have an insurance policy that cover cyber risks. On the other hand, only 6% of businesses have the Cyber Essential certification and 1% have Cyber Essentials plus, which is largely due to relatively low awareness.
Chapter 1: Introduction
1.1 Code of practice for statistics
The Cyber Security Breaches Survey is an official statistic and has been produced to the standards set out in the Code of Practice for Statistics. The code is based on three pillars: trustworthiness, quality and value. To this end we have quality assured all the figures presented throughout this report to match the raw survey outputs, considered all statements to be contextually appropriate, and used a writing style to ensure it is fit for a wider audience.
1.2 Background
Publication date: 30 March 2022
Geographic coverage: United Kingdom
The Department for Digital, Culture, Media and Sport (DCMS) commissioned the Cyber Security Breaches Survey of UK businesses, charities and education institutions as part of the National Cyber Security Programme. The findings of this survey provide a comprehensive description of cyber security for a representative sample of UK organisations, which provides a snapshot of cyber resilience at this current point in time. It therefore tells us what organisations are doing to stay secure, and also details the cyber threat landscape. It also supports the government to shape future policy in this area, in line with the National Cyber Strategy 2022
Survey interviews are conducted by the market research provider Ipsos UK. The project requirements and reporting are finalised by DCMS and for the 2022 publication includes:
- Cyber Security policies and processes
- Technical controls and governance for cyber security
- Board level attitudes and strategy for cyber security
- Areas of interest such as cyber security training, supply chain risk management, use of government guidance
- Cyber threat landscape, including the impacts, outcomes and estimated financial cost
- Incident response to cyber breaches
This 2022 publication follows previous surveys in this series, published annually since 2016. In each publication year, the quantitative fieldwork has taken place in the winter of the preceding year (for example, in winter 2021/22, for this latest survey). This Statistical Release focuses on the business and charity outcomes. The results for educational institutions have been included in a separate Education Annex
1.3 Methodology
As in previous years, there were two strands to the Cyber Security Breaches Survey:
- We undertook a random probability telephone survey of 1,243 UK businesses, 424 UK registered charities and 420 education institutions from 16 October 2021 to 21 January 2022. The data for businesses and charities have been weighted to be statistically representative of these two populations.
- Random Iterative Method (RIM) weighting has been applied to the survey raw data so as to ensure it is proportionate to the profile of UK organisations, with respect specifically to size and sector. All figures quoted in this report are from the weighted outputs. It should be noted that as BEIS business populations show; the composition of UK businesses is mostly micro and small, which is reflected in any overall figures in this report.
- We carried out 35 in-depth interviews between December 2021 and January 2022, to gain further qualitative insights from some of the organisations that answered the survey. Sole traders and public-sector organisations were outside the scope of the survey. In addition, businesses with no IT capacity or online presence were deemed ineligible. These exclusions are consistent with previous years, and the survey is considered comparable across years. The educational institutions, covered in the separate Education Annex, comprise 198 primary schools, 221 secondary schools, 34 further education colleges and 37 higher education institutions. More technical details and a copy of the questionnaire are available in the separately published Technical Annex.
1.4 Changes since the 2021 survey
The 2022 survey is methodologically consistent with previous years, in terms of the sampling and data collection approaches. This allows us to look at trends over time with confidence, where the same questions have been asked across years. However, this year’s study makes the following important changes:
- A small number of questionnaire changes to stay in line with DCMS policy objectives (e.g., new questions related to ransomware and managing supplier risks).
- The business sample for the 2022 publication is 12% smaller than the previous year due to homeworking practices creating significant challenges in contacting survey respondents. Any changes to the survey which result in findings no longer being comparable with previous years are flagged in the Statistical Release. These changes can be found in the Technical Annex. In particular, the changes to the cost data mean we can no longer make direct comparisons to previous years, but can still comment on whether the pattern of results is similar to previous years.
1.5 Interpretation of findings
How to interpret the quantitative data
The survey results are subject to margins of error, which vary with the size of the sample and the percentage figure concerned. For all percentage results, subgroup differences have been highlighted only where statistically significant (at the 95% level of confidence).[footnote 1] [footnote 2] This includes comparison by size, sector, and previous years. By extension, where we do not comment on differences across years, for example in line charts, this is specifically because they are not statistically significant differences. There is a further guide to statistical reliability at the end of this release.
Subgroup definitions and conventions
For businesses, analysis by size splits the population into micro businesses (1 to 9 employees), small businesses (10 to 49 employees), medium businesses (50 to 249 employees) and large businesses (250 employees or more). For charities, analysis by size is primarily considered in terms of annual income band. The sample size for charities (424) has slightly decreased this year compared to the slightly larger 2021 sample size (487). However, we have still been able to highlight income band differences, with the greatest focus being on the subgroups of high-income charities (with £500,000 or more in annual income) and charities with very high incomes (of £5 million or more).
Due to the relatively small sample sizes for certain business sectors, these have been grouped with similar sectors for more robust analysis. Business sector groupings referred to across this report, and their respective SIC 2007 sectors, are:
- administration and real estate (L and N)
- agriculture, forestry and fishing (a)
- construction (F)
- education (P)
- health, social care and social work (Q)
- entertainment, service and membership organisations (R and S)
- finance and insurance (K)
- food and hospitality (I)
- information and communications (J)
- utilities and production (including manufacturing) (B, C, D and E)
- professional, scientific and technical (M)
- retail and wholesale (including vehicle sales and repairs) (G)
- transport and storage (H).
Analysis of organisation cyber security split by geographical region is considered to be out of the scope of this reporting. While we have and may occasionally provide data specific for ITL 1 regions, we do not believe there to be substantial correlation for this cross-break. Regional differences may also be attributable to the size and sector profile of the sample in that region. Where figures in charts do not add to 100%, or to an associated net score, this is due to rounding of percentages or because the questions allow more than one response.
How to interpret the qualitative data
The qualitative survey findings offer more nuanced insights into the attitudes and behaviours of businesses and charities with regards to cyber security. The findings reported here represent common themes emerging across multiple interviews. Insights from an individual organisation are used to illustrate findings that emerged more broadly across interviews. However, as with any qualitative findings, these examples are not intended to be statistically representative.
1.6 Acknowledgements
Ipsos UK and DCMS would like to thank all the organisations and individuals who participated in the survey. We would also like to thank the organisations who endorsed the fieldwork and encouraged organisations to participate, including:
- the Association of British Insurers (ABI)
- the Charity Commission for England and Wales
- the Charity Commission for Northern Ireland
- the Confederation of British Industry (CBI)
- the Institute of Chartered Accountants in England and Wales (ICAEW)
- Jisc, a not-for-profit company that provides digital infrastructure, services, and guidance for UK further and higher education institutions.
- Universities and Colleges Information Systems Association (UCISA)
Chapter 2: Profiling UK businesses and charities
Organisations are more likely to suffer a breach if they increase their digital footprint, use Managed Service Providers (MSPs), or allow employees to use personal devices. This chapter covers the types of organisations that tend to be more exposed to these types of risks. It helps to contextualise some of the sector differences evidenced in later chapters.
2.1 The digital footprint of different organisations
Almost all organisations have some form of digital exposure. Over nine in ten businesses (92%) and eight in ten charities (80%) have at least one of the items listed in Figure 2.1. These are in addition to having their own websites and staff email accounts – something we have recorded as being near-universal in previous years of the survey.
Only a minority of businesses and charities take payments or bookings online. Medium (40%) and large (48%) businesses are more likely than the business average (30%) to have such payment capabilities, as are high-income charities (46% vs. 31% overall).
Network-connected devices (sometimes called smart devices) were more common amongst businesses than last year (48% vs. 46%). These can be devices such as TVs, building controls, alarms or speakers, among others. These are more commonplace in businesses than charities (48% vs. 29%). Larger organisations also report using these devices more often (66% of medium firms, 82% of large firms and 66% of high-income charities do so).
Figure 2.1: Percentage that currently have or use the following digital services or processes.[footnote 3]
| Digital service or process | Businesses | Charities |
|---|---|---|
| Online bank account | 80% | 59% |
| Personal information about customers held electronically | 61% | 61% |
| Network-connected devices^ | 48 % | 29% |
| Ability for customers to order, book or pay online | 30% | 31% |
Bases: Total: 1,243 UK businesses; 424 charities. Half A: 658 UK businesses; 185 charities ^Only asked of sample half A
We ask charities separately about two types of online activity that might affect them, over and above private sector businesses:
- Just over four-in-ten charities (44%) allow people to donate to them online.
- Around four-in-ten (42%) have beneficiaries that can access services online.
It is more common for high-income charities to allow people to donate to them online (65% of those with £500,000 or more) and to have beneficiaries that can access services online (54%) when compared to charities overall.
Sector differences
Among businesses, the sectors that are most likely to hold personal data about customers include:
- finance and insurance (85%, vs. 61% businesses overall)
- health, social work, and social care (81%)
The sectors where it is most common for customers to book or pay online are, as might be expected, the food and hospitality sector (49%, vs. 30% businesses overall) and the retail and wholesale sector (42%). The sectoral differences for finance, health, and food and hospitality industries are broadly in line with what we have found in previous years.
Food and hospitality firms are also more likely than others to use network-connected devices (59%, vs. 48% overall). The same can be said for the information communication sector (62%).
Trends over time
In 2021, businesses had adjusted their ability to deal with their finances online: more had online bank accounts (82% vs. 75% in 2020) and were able to accept online payments (30% vs 23% in 2020). This year’s results show similar results: 80% of businesses had an online bank account, and 30% of businesses accepted payments online. This suggests that businesses have either yet to recover from the impact of COVID-19, or they have adjusted to the ‘new normal’ in light of the pandemic.
2.2 Use of Managed Service Providers (MSPs)
This year, for the first time, we asked organisations whether they used a Managed Service Provider (MSP). An MSP is a supplier that delivers a portfolio of IT services to business customers via ongoing support and active administration, all of which are typically underpinned by a Service Level Agreement. An MSP may provide their own Managed Services or offer their own services in conjunction with other IT providers’ services. As shown in Figure 2.2., four in ten businesses (40%) and almost a third of charities (32%) use at least one MSP.
Figure 2.2: Percentage that use a Managed Service Provider (MSP)
Bases: 1,243 UK businesses; 696 micro firms; 264 small firms; 149 medium firms; 134 large firms; 82 finance/insurance; 424 charities
The use of MSPs was more common amongst medium-sized businesses (65%) and large businesses (72%). The use of MSPs is more common in the financial and insurance industries than businesses overall (70% vs. 40%). The financial services sector is highly regulated, offers more complex products, and poses a legitimate target for cyber attack. All of these provide a reason for firms in this sector to opt for the quality and assurance that can be provided by an MSP. High-income charities (with £500,000 or more in annual income) were also more likely to use MSPs (68% vs. 32% overall).
In the qualitative strand, we found that organisations used a variety of MSPs. Across organisations as a whole these tended to relate to cloud based services hosting emails or external data storage. Though less likely to use them, smaller organisations tended to use MSPs for services where they were unlikely to have a team of specialist staff. These included central service functions such as payroll, HR, and IT.
We then asked about the procurement processes, specifically if cyber security was considered as an important factor when selecting an MSP. Overall cyber security was not an important factor, especially amongst smaller organisations selecting MSPs for central functions. They prioritised the price of procuring the MSP as well as the overall quality of service they would offer. When selecting an email provider or data storage providers, cyber security was seen as a priority, but was not considered during procurement. Instead, they assumed that the providers would have excellent cyber security, far better than their own, owing to the fact they were often multinational technology companies.
However, organisations will often require that suppliers, including MSPs, prove they have robust cyber security when signing contracts. Once the contract is signed, though, this is not often followed up with extensive due diligence or measurement of KPIs, and risks are not reviewed throughout the duration of the relationship.
2.3 Use of personal devices
Using a personal device, such as a personal non-work laptop, to carry out work-related activities is known as bringing your own device (BYOD). Nearly half of businesses (45%) and two-thirds of charities (64%) say that staff in their organisation regularly do this, as Figure 2.3 shows.
BYOD has historically been more prevalent in charities than in businesses (since charities were first included in the 2018 survey). DCMS’s 2017 qualitative research with charities suggested that this behaviour was especially common among smaller charities. It found that they often have lower budgets for IT equipment or do not have their own office space, so have previously been more likely to encourage home working. This behaviour is also more common among entertainment, service and membership organisations.
Figure 2.3: Percentage that have any staff using personally owned devices to carry out regular work-related activities
Bases: 1,243 UK businesses; 696 micro firms; 264 small firms; 149 medium firms; 134 large firms; 146 prof/sci/technical; 424 charities
The business findings show similar results to 2021 in reported BYOD this year (45%, vs. 47% in 2021). This is counter to the long-term trend. However, this could be a reporting issue rather than a true change in the use of personal devices. For example, organisations may have less oversight of how staff working from home are accessing their files or network.
2.4 Older versions of Windows
We asked organisations if they had computers with old versions of Windows installed (i.e., Windows 7 or 8). The National Cyber Security Centre (NCSC) and others have previously highlighted that some older versions (pre-Windows 8.1) have stopped being supported, so may be more vulnerable to cyber security breaches. As Figure 2.4 shows, 16% of businesses and 14% of charities say they still have older versions of Windows installed.
Figure 2.4: Percentage or organisations that have older versions of Windows installed
Bases: 593 UK businesses; 334 micro firms; 122 small firms; 64 medium firms; 73 large firms; 85 utilities/production; 250 charities; only asked of sample half B
Having older versions of Windows is more common among large businesses (23%, vs. 16% overall) and those in the utilities and production sector (26%). It is less common in the finance and insurance sector (11%), with other sectors being relatively close to the average.
Chapter 3: Awareness and attitudes
This chapter starts by exploring how much of a priority cyber security is to businesses and charities, and how this has changed over time. It also looks at where organisations get information and guidance about cyber security, how useful this is for them and what they have done in response to seeing or hearing official guidance. In the qualitative research we explore how organisations discuss and make decisions on cyber security.
3.1 Perceived importance of cyber security
Eight in ten businesses (82%) report that cyber security is a high priority for their senior management, representing an uplift on last year (77%). Seven in ten charities (72%) say their trustees believe cyber security is a high priority. This is significantly lower than the figure for businesses and consistent with last year. As illustrated in Figure 3.1 and as found in the last survey, for both groups there is an approximately equal split between those that say it is a very or fairly high priority.
The respondent taking part in the interview is the individual at their organisation with responsibility for cyber security. In smaller organisations, this is likely to be someone in the senior management team, who can answer this question first-hand. In larger organisations, these individuals may not be senior managers, and their answers will reflect their own perceptions of their senior management teams.
Figure 3.1: Extent to which cyber security is seen as a high or low priority for directors, trustees and other senior managers
| Organisations | Very high | Fairly high | Fairly low | Very low | Don’t know | Overall |
|---|---|---|---|---|---|---|
| Businesses | 37% | 44% | 13% | 4% | 1% | 82% |
| Charities | 33% | 39% | 14% | 12% | 3% | 72% |
Bases: 1,243 UK businesses, 424 charities
It is more common for larger businesses to say that cyber security is a high priority (92% of medium businesses and 95% of large businesses, vs. 82% overall, as shown in Figure 3.1). The same is true for high-income charities (92% of those with income of £500,000 or more, vs. 72% of charities overall). Almost all the very largest charities (with incomes of £5 million or more) say their trustees give cyber security a high priority (97%).
In previous years three sectors have consistently treated cyber security as a higher priority than others, and this continues to be the case. Once again, the sectors that attach the highest priority to cyber security are:
- Finance and insurance (65% say it is a very high priority, vs. 38% of all businesses);
- Health and social care (59% very high priority);
- Information and communications (58% very high priority).
While fewer than three in ten entertainment, service, and membership organisations (28%) place a very high priority on cyber security, almost seven in ten (67%) give it a fairly high priority. This combined figure of 95% puts the sector above most others. By contrast, and in line with last year, food and hospitality businesses tend to regard cyber security as a lower priority than those in other sectors (only 66% say it is a high priority, vs. 82% of businesses overall).
Trends over time
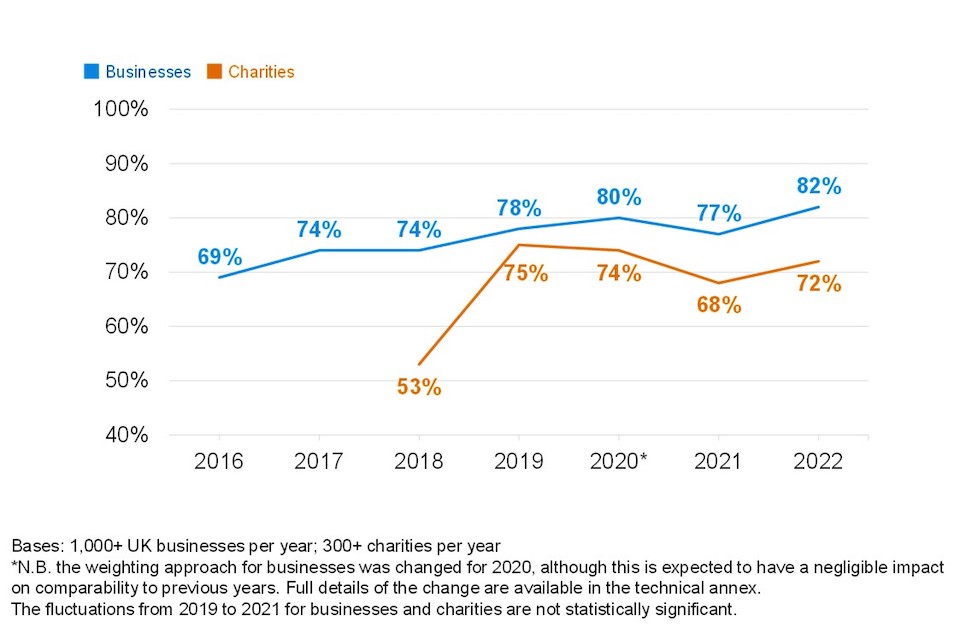
Figure 3.2 shows how the prioritisation score has changed over time and for businesses the increase since 2021 is now at an all-time high. This signifies a recovery from last year, where our qualitative research suggested that some organisations deprioritised cyber security to focus on business continuity (in light of the COVID-19 pandemic). While cyber security is now seen as a higher priority, we have not seen a corresponding increase in actions to implement enhanced cyber security.
The qualitative findings below suggest a number of challenges about how to translate board engagement with cyber security into increased cyber resilience amongst businesses. In qualitative interviews, organisations spoke of challenge around creating a clear commercial narrative that can be used in internal budget conversations, to ensure that cyber security is given appropriate investment against other competing business demands. There is a lack of understanding of what constitutes effective cyber risk management, which is compounded by a lack of expertise and perceived complexity of cyber security matters at board level.
Despite an increased figure for charities, a lower base size means this was not statistically significant. As noted in previous years, the more substantial rise for charities between 2018 and 2019 is likely to have been driven by the introduction of the General Data Protection Regulation (GDPR) in early 2018.
Figure 3.2: Percentage of organisations over time where cyber security is seen as a high priority for directors, trustees and other senior managers
3.2 Involvement of senior management
How often are senior managers updated on cyber security?
Figure 3.3 breaks down how often senior managers get updates on the state of cyber security and any actions being taken. It shows that updates tend to be more frequent in businesses than in charities, continuing a trend from previous years.
With figures that are almost identical to the last survey, half of businesses (50%) update their senior team at least quarterly, while four in ten charities (42%) also do this. Two-thirds of businesses (65%) and six in ten charities (60%) say senior managers are updated at least once a year.[footnote 4] This is in addition to those saying senior managers are updated every time a breach occurs (6% of businesses and 4% of charities). Almost a quarter (23%) of charities say they never update their senior management on actions taken around cyber security (compared to 16% of businesses).
Figure 3.3: How often directors, trustees or other senior managers are given an update on any actions taken around cyber security
| Organisations | Never | Less than once a year | Annually | Quarterly | Monthly | Weekly | Daily | Each time there is a breach | Don’t know |
|---|---|---|---|---|---|---|---|---|---|
| Businesses | 16% | 7% | 15% | 15% | 15% | 10% | 10% | 6% | 6% |
| Charities | 23% | 7% | 18% | 20% | 15% | 4% | 3% | 4% | 5% |
Bases: 1,243 UK businesses; 424 charities
As in previous years, this varies greatly by the size of the organisation. Among large business, eight in ten (80%) have senior managers updated at least quarterly and within medium sized enterprises it is around seven in ten (68%). This contrasts with the situation among micro and small businesses, within which just under half (49%) provide updates at least quarterly.
Six in ten (61%) high-income charities provide quarterly updates to their trustees. A figure that rises to almost eight in ten (77%) among the very largest charitable organisations (income of at least £5 million) covered by the survey. There is wide variance by sector regarding the frequency with which senior managers are updated on cyber security actions. In three sectors at least a fifth never update their senior management. These are:
- Food and hospitality (26% never update senior managers vs. 16% of all businesses);
- Utilities, production, or manufacturing (21%);
- Retail and wholesale (20%).
In contrast fewer than one in ten within financial and insurance (4%) or information and communications businesses (9%) never update senior managers on cyber security actions. In both these sectors, around seven in ten (72%) provide cyber security updates at least quarterly (compared to 50% for all businesses).
Board responsibilities
Around one third of businesses (34%) and one quarter of charities (26%) have board members or trustees accountable for cyber security as part of their job (Figure 3.4). The figure for charities represents statistically significant decline since the previous survey (35% in 2021).
As might be expected, this is much more common in larger organisations, where the management board is likely to be larger. Six in ten large enterprises (62%) have a board member responsible for cyber security.
This is not the case in charities. Across five income bands the proportion of charities reporting they have a trustee with responsibility for cyber security occupies a tight range of 25% to 29%.
Figure 3.4: Percentage of organisations with board members or trustees that have responsibility for cyber security
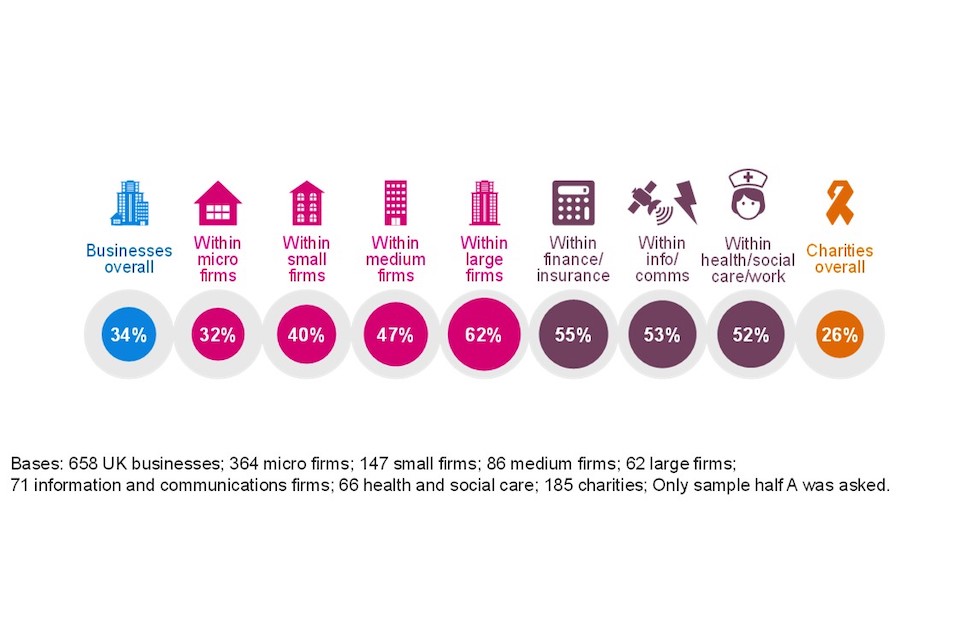
Finance and insurance firms (55%), information and communications firms (53%), and health and social care providers (52%) are all more likely than average to have board members taking responsibility for cyber security. The first two of these sectors were also above average in the 2021 survey. At the other end of the scale, construction firms (20%), agriculture (23%) and food and hospitality firms (25%) are among the least likely to have board members assigned this role.
Trends over time
The proportion of businesses saying that senior managers have never been updated on cyber security has remained stable for the past four years (Figure 3.5). This suggests that cyber security is being discussed in boardrooms more than it was in 2016 and 2017, but despite high profile instances of cyber attacks over the last few years it is not moving any further up the agenda.
The proportion of charities saying they never update senior managers on cyber security (23%) is identical to 2021 and is close to the 2019 level. This strengthens the view expressed last year that the 2020 result could be an outlier. In the longer term, the result is more positive than the (pre-GDPR) 2018 survey. Qualitative interviews suggest that those at senior level within charities may lack the skill to address cyber security or be focused on other issues.
Figure 3.5: Percentage of organisations over time that never update senior managers on any actions taken around cyber security
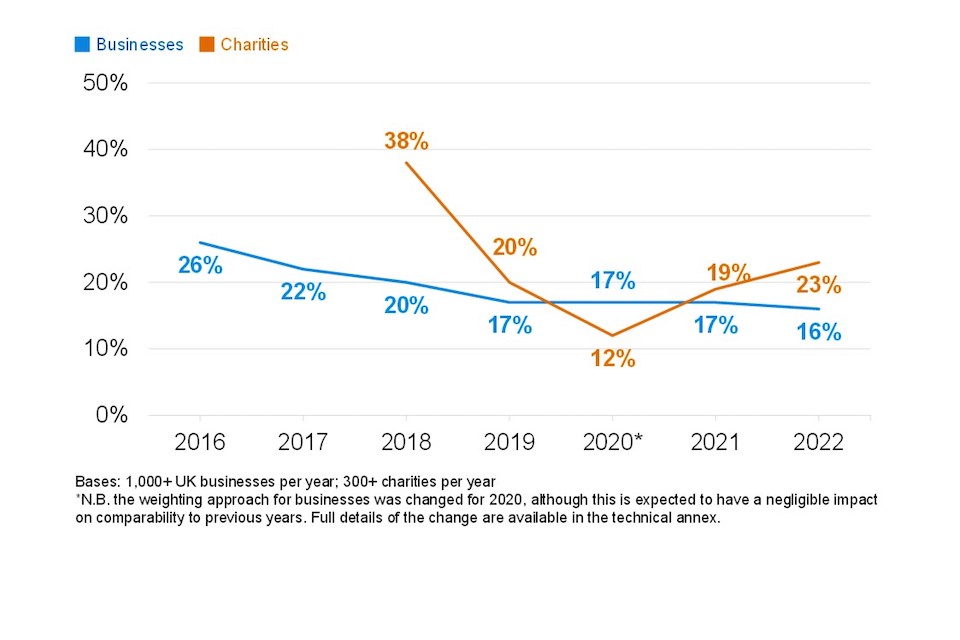
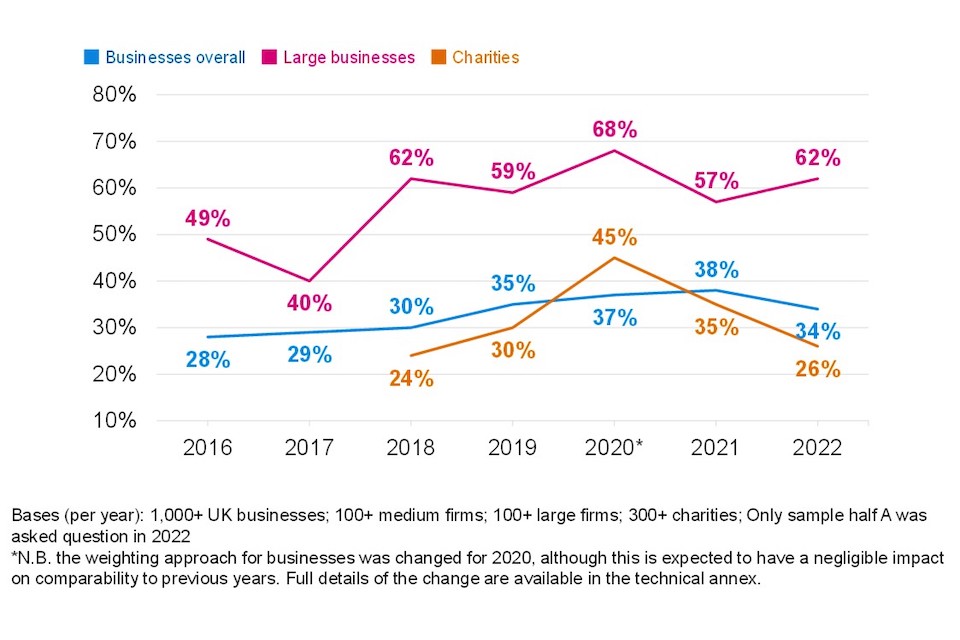
Figure 3.6 shows the trend over time for board members taking on cyber security responsibilities. Among businesses this has been relatively flat over the past four years, but it remains the case that more board members are taking on cyber security roles than was the case in 2016 or 2017. For large businesses, this proportion has increased since 2021 to be in line with the 2018 and 2019 results.
Among charities, the latest result represents a significant drop since 2021 and is close to the level recorded in 2018. Qualitative research below implies that charities have decided they face greater challenges than cyber security and need to prioritise those, with fundraising revenue impacted by the pandemic. Whatever the case, the latest result suggests that the 2020 result may represent an outlier in terms of the long-term trend among charities.
Figure 3.6: Percentage of organisations over time with board members or trustees with responsibility for cyber security
3.3 Cyber security decision making
Decisions on budgeting and approaches to cyber security
A lack of board level expertise presented a significant barrier to securing the appropriate level of funding, and driving the right action in terms of an organisations overall cyber security approach. Qualitative interviews demonstrated competition for budget against other business demands. A lack of viable commercial narrative, lower perceived importance, and lack of understanding even amongst larger organisations lead to a more reactive approach as we have identified previously. The interviews found a key enabler of cyber resilience is educating the board on key threats as well as prudent cyber risk management. Often organisations are dependent on a staff member with expertise to effectively communicate this to board level.
There tended to be an awareness and acknowledgement of cyber risks at a high level. However, boards tend to trust and defer the finer details of a cyber security approach to their IT teams (in the case of larger organisations) or third parties and external providers (in the case of smaller organisations). This is because there was a low level of knowledge of the technical details of cyber risks and how to manage them at senior management and board level. There was a lack of serious understanding of the risks outside of specialist staff within organisations. However, those with specialist staff within the company or a network of specialist advisers or third parties were better able to make decisions favouring cyber security.
“We take our lead from IT. They would bring to our attention something and say if your system isn’t at this level, there’s a good chance you could get hacked so we really leave them to make sure that we are as protected as possible. If they said to us, you could have this all singing all dancing set up, but it would cost you 10 grand, you’d probably say no thanks… they’d have to make a business case.” Large charity
Larger organisations often had a more layered approach to decision making:
- In larger organisations, the cyber security budget would often be part of a wider IT budget. Senior IT or cyber security staff would present their plans to board. Boards would often trust their judgement on technical details on suggested approaches to cyber security, but there were often challenges around making the business case for change. This meant they were competing with other departments for money, and it was up to the boards to decide how much investment cyber security should have. Often this led to more immediate or tangible risks (such as physical security of premises) being prioritised over cyber security.
- In some larger organisations there were cyber security experts in senior roles. This made it easier for organisations to make the business case for increased cyber security spending. In turn, this allowed them to have a cyber security sponsor on the board who could champion more complex controls, such as threat intelligence or penetration testing. A senior leader with good understanding of cyber security improved the knowledge of other board members. This increased awareness amongst the wider body of staff.
“They are very much involved in the top-level budget, and if it’s anything above a threshold, and it’s not a defined threshold of 500 pounds or 5000 if it’s something that I deem that actually the board should be aware of, they need to make a decision that is strategic. I’ll brief them, and they’ll make a decision. Generally, the day to day running [of cyber security] is left to myself.”
Large business
In smaller organisations there was a low level of internal cyber security expertise. Often this meant that decisions relating to cyber security were made as part of wider initiatives. For instance, a small charity stated that they ensured their data was stored on a cloud provider and encrypted. However, they also stated this was driven by a desire to protect sensitive data and comply with GDPR regulations as opposed to ensuring the organisation had robust cyber security. This meant that they did not have fixed cyber security budgets. Instead, investment was secured if improving cyber security was deemed as important to the future direction of the organisation or mitigated potential risks.
Challenges on cyber security decision making
Despite high prioritisation shown in figures 3.1 and 3.2 there are many factors across organisations that make decision making challenging and inhibit a good cyber security approach. This may help explain why many metrics by which we measure cyber resilience in Chapter 4 have either flatlined or declined over the past two years.
Ultimately, and as mentioned previously, there was a lack of knowledge of cyber security at a senior level. Even for exceptions where organisations had senior leaders with cyber expertise, this tended to be accidental, and their core role did not explicitly relate to cyber security. Therefore, there was a consistent challenge to convince management of the seriousness and strategic threat cyber attacks posed. Senior leaders tended to be focused on day-to-day priorities instead, with this being exacerbated during the COVID-19 pandemic.
There were also challenges that were specific to certain types of organisations. Typically, in larger organisations:
- The lack of expertise on board sometimes fostered a lack of curiosity in cyber security policy. This led to more reactionary measures (e.g., boosting security to comply with GDPR) as opposed to taking a pro-active stance on cyber security. However, that is not to say they did not trust their IT staff with cyber security.
- The high level of trust in cyber security staff amongst boards can sometimes present a challenge. It is often on IT or cyber security staff to make a good case for cyber security risks being present and investment to mitigate them. This was often not in their core skillset, meaning important risks were deprioritised and budget went elsewhere. Therefore, it was critical that boards balanced the trust they had in their IT staff with their own ability to judge a business case on its technical merits.
Smaller organisations took little proactive action on cyber security, driven by a lack of internal knowledge and competing priorities with their budgets. This was especially the case if they had no relationships with outsourced cyber security providers or IT specialist MSPs. They often had a fear of the technicalities of cyber security and a preference to not research and mitigate against the risks they presented. They knew there could be a potentially devastating impact, but were not sure of the specifics of this, and felt it was low probability. This meant budget priorities often focused on the immediate operational side of the organisation.
“I think it’s just been something that we’ve known the word cybersecurity, but never thought given the scale and size of our business, that it’s something that we need to worry about. It’s something that banks and government departments need to be concerned about in terms of data breaches. It’s not something that is his concern for us.” Small business
Though this challenge did affect all organisations, there was a particular issue with charities on a lack of focus or aim when it came to cyber security. A lack of new regulations to enforce meant that charities felt there was no immediate need to prioritise cyber security in a way they had done when GDPR became law.
In order to overcome these challenges IT teams had to engage boards through how they framed cyber security. Boards were more receptive if they viewed cyber security as a threat to business continuity carrying an operational or financial risk. This allowed them to visualise the impact a serious breach could have and made facilitating discussion and, ultimately, securing the desired budget more straightforward. Conversely, board members were less likely to engage if it was presented solely as an IT issue. Some organisations, particularly smaller charities, had started to attempt to overcome the challenges and their own lack of expertise in this area by joining networks of CEOs or other organisation leaders to tackle cyber security.
“[Training and briefing board] was to frame their understanding of the risk of the impact of non-compliance… If they understand the risk and the impact of the business and then as directors, it will frame them in making decisions. And it was worthwhile because they don’t challenge me, but they understand why I’m saying that. We need to update all of our Windows because when new ones coming in, if it’s not patched and it’s not updated. It’s going to cost the business.” Large business
3.4 Sources of information
Overall proportion seeking cyber security information or guidance
We ask organisations where they seek information, advice, or guidance on the cyber security threats they face. It is then determined whether the sources sit within their organisation or are an external source. External sources include government sources, third party cyber security or IT providers, trade bodies, or general sources such as an internet search or from the media. Around half of businesses (48%) and approximately four in ten charities (41%) report actively seeking information or guidance on cyber security from outside their organisation in the past year.
As Figure 3.7 illustrates, external information is more often sought by small, medium, and large businesses, rather than micro firms where a minority has taken such action. The sectors where firms are most likely to seek out external information are finance and insurance (68%), information and communications (60%) and professional, scientific, and technical (60%).
Larger charities seek external information to a much greater degree than their smaller counterparts. Seven in ten charities with an income of £500k or more (72%) sought external information compared to under four in ten charities with an income of less than £100k (37%).
For businesses overall, this result is lower than in 2021 (53%). It is similar to the peak observed in 2018 and 2019 (59%), following the implementation of GDPR. For large businesses specifically, the figure of 68% is also lower than last year (75%) but remains above 2020 (57%) and 2019 (64%). This may indicate that the volume of large businesses seeking information during the COVID-19 pandemic is now subsiding.
For charities (41%), the latest result is in line with that seen over the course of the past few years, where the figure seeking external information has typically been around half or just under.
Figure 3.7: Proportion of organisations that have sought external information or guidance in the last 12 months on the cyber security threats faced by their organisation
As in 2021 a small minority of businesses and charities seek information internally within their organisations (3% of businesses and 7% of charities).
Where do organisations get information and guidance?
As in previous years, the most common individual sources of information and guidance are:
- external cyber security consultants, IT consultants or IT service providers (mentioned by 25% of all businesses and 18% of all charities);
- general online searching (8% of businesses and 5% of charities);
- any government or public sector source, including government websites, regulators, and other public bodies (8% of businesses and 10% of charities).
These have also been the most frequently mentioned sources in previous years. The huge range and diversity of individual sources mentioned, together with the relatively low proportions for each, highlights that there is still no commonly agreed information source when it comes to cyber security. For example, just one per cent of both businesses and charities overall mention the National Cyber Security Centre (NCSC) by name. Among charities, fewer than one in ten (7%) mention charity-specific sources such as their relevant Charity Commission.[footnote 5]
Awareness of government guidance, initiatives and communications
The unprompted question around information sources tends to underrepresent actual awareness of government communications on cyber security, as during a live interview people cannot always recall specific things they have seen and heard, often a relatively long time ago. We therefore asked organisations whether they have heard of specific initiatives or communications campaigns before. These include:
- The national Cyber Aware communications campaign, which offers tips and advice to protect individuals and organisations against cybercrime;
- the 10 Steps to Cyber Security guidance, which aims to summarise what organisations should do to protect themselves;
- the government-endorsed Cyber Essentials scheme, which enables organisations to be certified independently for having met a good-practice standard in cyber security.
Figure 3.8 illustrates that awareness of these schemes and initiatives is broadly unchanged from the previous survey. More have heard of Cyber Aware than the other schemes, but still only a minority of businesses and charities are aware of each one.
Figure 3.8: Percentage of organisations aware of the following government guidance, initiatives or communication campaigns
| Government guidance | Businesses | Charities |
|---|---|---|
| Cyber Aware campaign | 30% | 38% |
| The Cyber Security Board Toolkit | 17% | 11% |
| 10 Steps guidance | 17% | 20% |
| Cyber Essentials scheme | 16% | 19% |
| Any Small Business Guides, such as the Small Business Guide to Cyber Security | 16% | 18% |
Bases: 1,243 UK businesses; 424 charities
Firms operating within the professional, scientific, and technical; financial and insurance; and information and communications sectors, tend to be more aware of these schemes or campaigns. Medium and large firms are also substantially more aware of these guidance packages, as are the larger charities, as shown below:
- Cyber Aware:
- 51% of medium firms and 49% of large firms
- 38% in both professional, scientific, and technical, and financial and insurance
- 47% of charities with £500k plus income, 62% in £5 million plus
- 10 Steps guidance:
- 34% of medium firms and 38% of large firms
- 26% in financial and insurance, 24% in information and communications
- 34% of charities with £500k plus income, 53% in £5 million plus
- Cyber Essentials:
- 49% of medium firms and 62% of large firms
- 36% in information and communications, 28% in both professional, scientific, and technical, and financial and insurance
- 43% of charities with £500k plus income, 76% in £5 million plus
There tends to be little difference between UK regions when it comes to attitudes and awareness towards cyber security. Therefore, it is noteworthy that in Scotland awareness of both Cyber Aware (43%) and 10 Steps guidance (25%) is higher than businesses elsewhere.
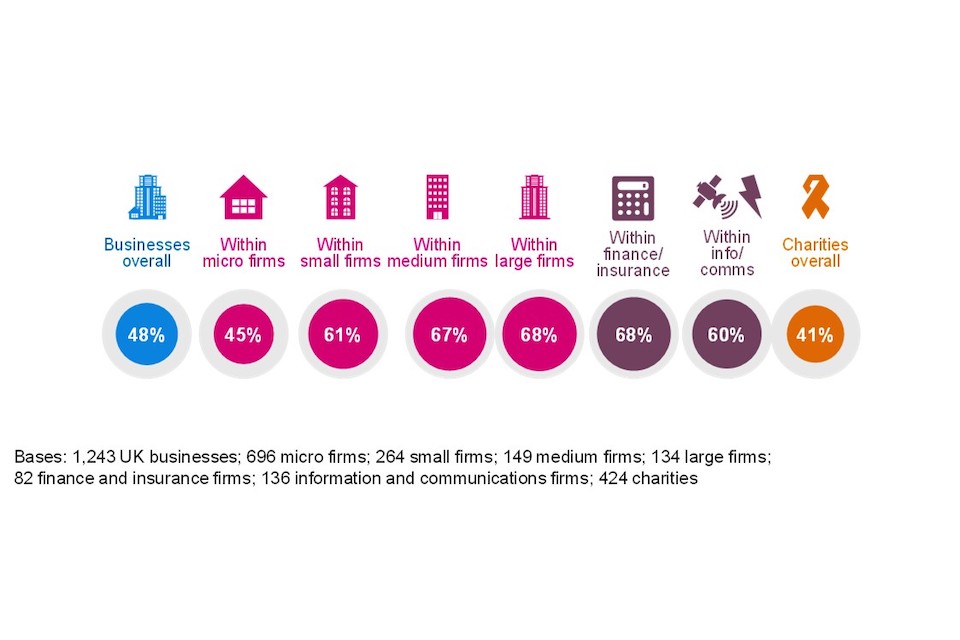
As Figure 3.9 shows, awareness of Cyber Essentials continues to gradually increase year on year. However, awareness of Cyber Aware and Ten Steps has remained at the same level for three consecutive years.
Figure 3.9: Awareness of government initiatives amongst businesses
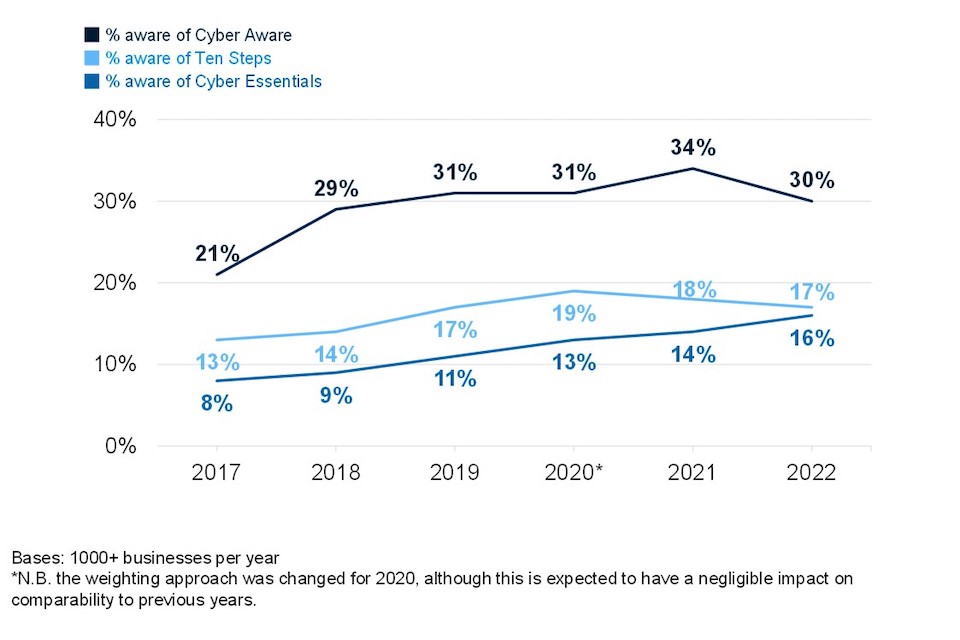
Although it still amounts to no more than a fifth of charities, among these organisations’ awareness of Cyber Essentials (19%) has increased significantly since 2021 (10%). However, awareness of Cyber Aware and Ten Steps is unchanged from last year and remains eight percentages points higher than in 2018 (when charities were first included in the survey).
Guidance targeted at specific types of organisations
We also asked again this year about NCSC guidance that is directed to specific sizes of business or towards charities. This includes:
- The NCSC’s Small Business Guide and Small Charity Guide, which outline more basic steps that these smaller organisations can take steps to protect themselves; and
- The NCSC’s Board Toolkit, which helps management boards to understand their obligations and to discuss cyber security with the technical experts in their organisation. For these sets of guidance, we find that:
- 16% of micro and small firms have heard of the Small Business Guide (unchanged from 18% in 2021)
- 18% of charities have heard of the Small Charities Guide (consistent with 2021)
- 14% of medium businesses have heard of the Board Toolkit (down from 18% in 2021, but still up from 11% in 2020)
- 27% of large businesses have heard of the Board Toolkit (compared to 24% in 2021).
Impact of government information and guidance
As outlined above in Figure 3.8, just under half of businesses (45%) and over half of charities (54%) have seen at least one of the initiatives or communications campaigns covered by the survey. As we did in 2021, this year we asked those that recalled seeing any of the government communications or guidance covered in the previous section an unprompted follow-up question. This explored whether exposure to the initiatives has led to them making changes to their cyber security.
In total, over four in ten businesses (44%) and charities (49%) report making changes to their cyber security measures as a direct response to seeing this government guidance. Both figures represent an increase since 2021 (37% and 38% respectively), suggesting that while ‘exposure’ may not have increased, organisations are now more motivated to act upon the guidance they see.
Across businesses, there is some variation by size. Micro businesses are notably less likely to have taken action as a result of hearing or seeing campaigns or guidance (41%), than those in small (56%) and large businesses (52%).
Among charities, two-thirds (66%) of those with an income of £500k or more that have seen relevant communications, also say they have made changes in response. The same figure is reported by charities with £5 million or more and is higher than the charity sector average of 49%.
In terms of the specific changes made, there are a wide variety of responses given, and no single response appears especially frequently. Only “changing or updating firewalls or system configuration” (10% of business and 9% of charities) and “changed or updated antivirus or antimalware software” (8% and 10%) were mentioned by approaching one in ten. Grouping specific comments into broad categories the following picture emerges:
- 25% of all businesses and 29% of all charities aware of campaigns and initiatives report making changes of a technical nature (e.g., to firewalls, malware protections, user access or monitoring). The figure for charities is a significant increase on last year (17%).
- Similar to 2021, 13% of businesses and 15% of charities say they have made changes to do with staffing (e.g., employing new cyber security staff), outsourcing or training. The third most common single response is to say they have implemented new staff training or communications (7% of businesses and 9% of charities).
- Also similar to last year, 15% of businesses and 16% of charities have made governance changes in response to seeing or hearing official guidance on cyber security.
Seeking and understanding information and guidance
In the qualitative interviews, we asked organisations about where they seek information or guidance on cyber security. Organisations had a range of different sources, such as providers of a cloud service, the government and information on the internet. Some organisations typically sought out information for a particular cyber security problem, which could be in response to an issue they had faced, or because of media reports about a specific cyber security problem. Some other organisations undertook a general search for information.
In larger organisations, information seeking tended to be proactive, and a constant part of their cyber security processes. Many of those interviewed described constant information seeking on cyber threats as part of their job role. Some large organisations used cyber security information forums (such as Jisc CISO, which focuses on threats to universities, and an energy-sector task group) to get the most up-to-date information on threats and some used the NCSC to find information about cyber threats, which provides good and up-to-date information. Organisations would also often seek out information in relation to a particular media story. Some would go on cyber security message boards, such as Darktrace, for the most up-to-date information on these. Some organisations believed that the government was not a useful source for information on current threats, due to how slow they can be in updating organisations on current threats.
Smaller organisations tended to seek out information on a reactive basis. This could be in response to a story in the media or a specific problem they were trying to address. Smaller organisations had a variety of sources they might call on, from specific experts on cyber security to general searches on the internet. The difference in information seeking between smaller and larger organisations is likely due to the extra capacity that larger organisations have; many have specific cyber security or IT teams to do this work for them. Competing priorities in day-to-day operations also impact the ability to seek out information on cyber security. In smaller organisations, there are many competing priorities which make regular information seeking difficult. Understanding of cyber security issues also impacted an organisation’s ability to seek out information and guidance. Some organisations found cyber security guidance overwhelming, due to the high level of knowledge they believed they would need to understand it.
Chapter 4: Approaches to cyber security
This chapter looks at the various ways in which organisations are dealing with cyber security. This covers topics such as:
- risk management (including supplier risks)
- reporting cyber risks
- cyber insurance
- technical controls
- training and awareness raising
- staffing and outsourcing
- governance approaches and policies.
We then cover the extent to which organisations are meeting the requirements set out in government-endorsed Cyber Essentials scheme and the government’s 10 Steps to Cyber Security guidance .
4.1 Identifying, managing, and minimising cyber risks
Actions taken to identify risks
The survey covers a range of actions that organisations can take to identify cyber security risks, including monitoring, risk assessment, audits, and testing. Organisations are not necessarily expected to be doing all of these things – the appropriate level of action depends on their own risk profiles.
Figure 4.1 shows the six actions covered by the survey. The most common actions remain deploying security monitoring tools and undertaking risk assessments. By contrast, penetration testing and threat intelligence are undertaken mostly by larger businesses suggesting smaller businesses may not have the funding to do this. These results are similar to those observed in 2021. Additionally, the ‘decline’ in security monitoring seen in 2020 (down from 40% to 35%), has not recovered. This could be because businesses continue to struggle to monitor multiple endpoints as remote working continues, where last year’s qualitative interviews highlighted this as a key issue.
Figure 4.1: Percentage of organisations that have carried out the following activities to identify cyber security risks in the last 12 months
| Activities | Businesses | Charities |
|---|---|---|
| Any of the listed activities | 54% | 41% |
| Used specific tools designed for security monitoring | 35% | 27% |
| Risk assessment covering cyber security risks | 33% | 26% |
| Tested staff (e.g. with mock phishing exercises) | 19% | 15% |
| Carried out a cyber security vulnerability audit | 17% | 14% |
| Penetration testing | 14% | 9% |
| Invested in threat intelligence^ | 14% | 10% |
Bases: 1,243 UK businesses; 424 charities; ^only asked half A, 658 UK businesses; 185 charities
As has been established in previous years, each of these actions are more common in medium and large businesses, as well as high-income charities (with £500,000 or more).
Looking at large businesses, at least half have taken each action. Investment in threat intelligence has the lowest take up at 52%. The figure rises to 67% for using specific tools such as intrusion detection systems. Among charities with an income of £5 million or more, cyber security risk assessment (67%) is the action taken most often. Although higher than their smaller counterparts, only a third (31%) of very high-income charities invest in threat intelligence.
Information and communications firms (74%) and finance and insurance firms (69%) continue to be more likely than the average business (54%) to have taken any of these actions. At the other end of the spectrum, construction firms (41%) and those in the food and hospitality sector (42%) are less likely to have done any of these things. This sectoral pattern is similar to previous years.
Qualitative insights on threat intelligence
This year we asked organisations about their awareness and use of threat intelligence, and whether the board had knowledge of threat intelligence. Some organisations viewed threat intelligence as a useful tool for keeping themselves aware of current problems. However, in other organisations there was a lack of awareness about what threat intelligence was, particularly in organisations which did not have a specific IT or cyber security team.
Some large organisations had threat intelligence from multiple sources, mostly external sources, including the NCSC and from clients and partners. Some organisations were part of intelligence-sharing portals which gave them information on current cyber threats. There was also third-party involvement, with some receiving intelligence on public vulnerabilities and foreign threats. This was seen to give them improved detection capabilities, as it would be difficult to acquire this kind of information in-house, due to competing priorities within an organisation. Organisations also used internal tools for threat intelligence: one organisation had an internal global cyber defence centre that managed threat intelligence for the firm. Some organisations chose not to purchase threat intelligence due to the cost, and used internal resources instead.
In smaller organisations, there was a lot of variation in the level of awareness of threat intelligence and some had no knowledge of what threat intelligence was. The threat intelligence received tended to be quite simple: for example, a payment provider making them aware of a current cyber threat, rather than information from a firm dedicated to threat intelligence.
“It might have been because we use software to constantly scan, update the system. But we don’t have cyber threat intelligence.” Small charity
How organisations undertake audits and implement their findings
Among the 17% of firms that undertake cyber vulnerability audits, similar proportions undertake internal audits (35% of businesses) or external audits (39%). One in five (21%) carry out both. The proportion conducting both internal and external audits has fallen eight percentage points since 2021; with those solely using external audits increasing (39% vs. 32% in 2021).
How businesses undertake audits is strongly linked to the size of the organisation:
- Micro businesses are most likely to solely use internal staff to undertake audits (39% of the micro firms undergoing any type of audit);
- Micro and small businesses have the greatest tendency to only use external contractors (39% and 42% respectively);
- Large businesses, likely having greater financial and personnel capacity, are most likely to state that audits have been undertaken both internally and externally (56%).
Fourteen per cent of charities have carried out cyber security vulnerability audits. Due to the lower overall sample size for such charities (effective base size of 41), this limits the ability to analyse the type of audit undertaken. Charities’ cyber security vulnerability audits are equally split between those conducted internally (33%), externally (30%) or by both parties (36%), but caution must be applied due to low base sizes.
Reviewing supplier risks
Suppliers can pose various risks to an organisation’s cyber security, for example in terms of:
- Third-party access to an organisation’s systems;
- suppliers storing the personal data or intellectual property of a client organisation;
- phishing attacks, viruses or other malware originating from suppliers.
While they undoubtedly exist, relatively few businesses or charities are taking steps to formally review the risks posed by their immediate suppliers and wider supply chain. As Figure 4.2 shows, just over one in ten businesses review the risks posed by their immediate suppliers (13%) and the proportion for the wider supply chain is half that figure (7%). Among charities the respective figures are even lower (9% and 5%).
The overall figures mask a wide variation by size of organisation. Possibly reflecting a more complex supply chain, nearly three in ten medium (27%) and over four in ten large businesses (44%) review the cyber security risks posed by their immediate suppliers. The respective figures for reviewing their wider supply chain are 12% and 26%.
Among charities with very high incomes, half (50%) have reviewed the risks posed by their immediate suppliers or partners and three in ten (29%) report looking at wider supply chain risks. The figures for reviewing supply chain risks represents a significant increase on last year, where the figure was 9%.
Reflecting a generally more sophisticated approach to cyber security overall, businesses in the finance and insurance (34%), and information and communications (28%) sectors are more likely than average (13%) to monitor the risks posed by their immediate suppliers. However, this year there are no significant sectoral differences as regards reviewing wider supply chains. Excluding transport and storage where the sample size is too small for reliable analysis, fewer than one in ten firms in any sector review the potential cyber security risks in their wider supply chain.
Figure 4.2: Percentage of organisations that have carried out work to formally review the potential cyber security risks presented by the following groups of suppliers
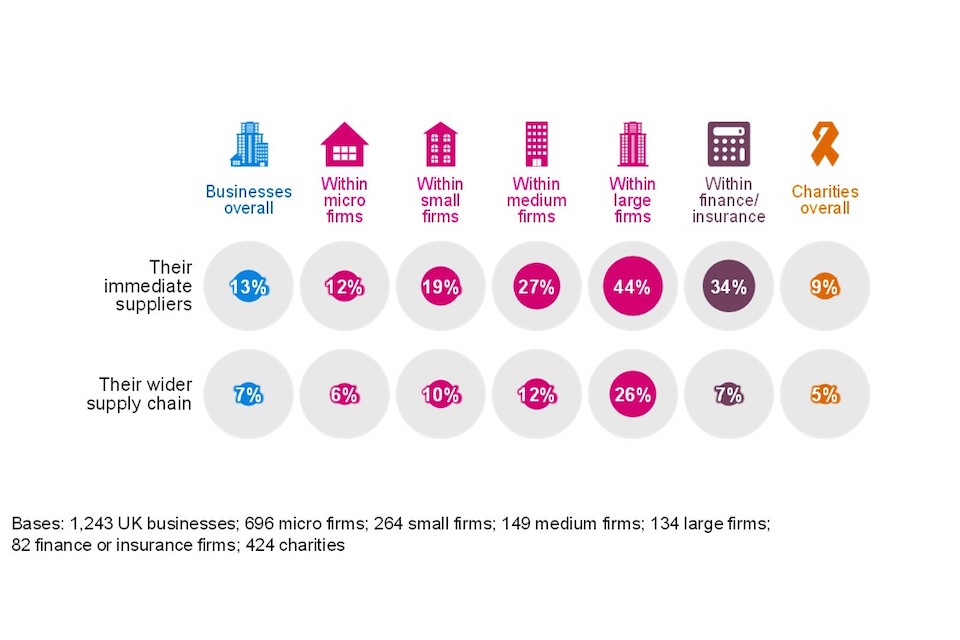
These results are broadly in line with the 2021 figures. It is worth noting though, following last year’s small but significant drop (9% in 2020 vs. 5% in 2021), the proportion of businesses saying they have reviewed wider supply chain risks (7%) now lies between that recorded in 2020 and 2021. Among large firms the figures for both immediate suppliers (44% vs. 36%) and the wider supply chain (26% vs. 20%), are higher this year than in 2021.
How and why organisations monitor supply chains
In the qualitative interviews, we talked to organisations about how they monitor their supply chain and how often they spoke with their suppliers about cyber security. Organisations did not see their supply chain as a serious risk, but some had consistent contact with suppliers. Some firms admitted that there tended to be some complacency at board-level when considering supplier risks.
There was a lot of variation in how organisations perceived their supplier risk. There tended to be some complacency around cloud-based suppliers: many organisations believed that these could not pose a threat to their own security. This was particularly apparent when discussing the cyber defences of ‘big tech’ companies, where organisations commonly perceived them to be invulnerable to cyber attacks.
“We’re now leveraging more client services; we have more suppliers hosting client services for us. Our own data centre footprint is drastically shrinking. We’re relying on suppliers to do more work on our behalf.” Large business
There was variation in the process of taking on a new supplier: some organisations had a formal process, perhaps with board-level involvement, whereas others (often smaller organisations) had no formal process. Some organisations took their supply-chain risk very seriously, and only dealt with suppliers on a one-to-one basis and would demand to see IT protocols. There was a belief amongst some organisations that supply-chain risk had increased in the past few years. Some organisations felt that the prominence of ransomware attacks in the media had caused them to think more about risks within their supply chains, despite the fact these two issues are not always related.
There was also variation amongst organisations in terms of how much contact they had with their suppliers. Of those who had contact with their suppliers, organisations said it was usually on an annual basis to discuss terms of a contract, but a small number of organisations kept up regular contact with suppliers, talking to them multiple times a week about concerns. There were also organisations who had never had contact with a supplier, once again citing their belief in the safety of big tech firms.
“I suppose I think I’m aware that the dialogues across the technical level regarding security patches are part of that ongoing dialogue, but it’s not kind of let’s sit down and talk about cybersecurity. One hopes that we’re using suppliers that are over the level of surety that that is just part and parcel of what they do. I think we’ve been very nervous about handing over access to a small one proven player.” Large business
Some small organisations felt their size prohibited them from reacting to risks from suppliers. For some organisations, the specific service a supplier provided meant they could not look elsewhere, even in the event of the supplier’s system being compromised.
Barriers to addressing supplier risks
Businesses that review supplier risks see the key barriers to addressing them as a perceived lack of time or money (36%). This is mentioned twice as often as not knowing which suppliers to check (18%), or a lack of relevant skills (18%). Almost one in three businesses (28%) cite a lack of information from suppliers as something that inhibits their ability to manage cyber security threats. The rank order and magnitude of each barrier is broadly consistent with last year’s survey.
Overall, nearly a third of businesses (32%) say none of the six factors prevent them from understanding potential cyber security risks within their supply chain. In 2021, the corresponding figure was 36%.
Figure 4.3: Barriers to businesses undertaking formal review of supplier or supply chain risks
Base: 269 UK businesses that have formally reviewed supply chain risks
As fewer than one in ten charities have reviewed supply chain risks, caution must be exercised due to the low base size. A perceived lack of time or money (46%) is the main difficulty charities face when seeking to understanding their supply chain cyber security risks. A third (33%) report that not knowing which checks to make is a limiting factor, but only 14% said a lack of prioritisation was limiting their work in this area.
Corporate reporting of cyber security risks
This year we asked organisations how cyber security is discussed in any publicly available annual reports. Very few businesses make annual reports publicly available and where they do, they tend not to cover the cyber security risks faced by their organisation. One in ten businesses (11%) published an annual report in the past 12 months, and among these the same proportion (11%) covered cyber security within it. Even across all sectors, no more than 15% of businesses publish an annual report.
Annual reports are more common amongst larger businesses, due to the range of stakeholders who must be involved, as well as the complexity of reporting on cyber security. Larger organisations are more likely to have the necessary resources for these. Four in ten (40%) large businesses published an annual report in the past 12 months. This compares to 25% of medium sized firms and 10% of micro/ small businesses. Within these reports, large businesses (30%) are significantly more likely than medium (16%) or micro/small (10%) businesses to publicly report on the cyber security risks they might face.
For many charities it is a statutory obligation to publish annual reports and with that, they are five times more likely than businesses to have done so within the past 12 months (54% vs. 11%). For charities with an income of £100,000 and above, the figure is at least 60%. However, fewer than one in twenty charities (4%) that have published an annual report in the past 12 months covered cyber security risks within it. The figure does rise to 14% in the very largest charities with incomes of £5 million or more.
In the qualitative interviews we asked organisations that mention cyber security in corporate reporting what this involved. Cyber security tended to be acknowledged as a risk, but the specifics were not assessed in any great detail. This was because cyber security was considered amongst a wider set of risks, meaning there was limited scope to go into detail. There was also little appetite to go into detail on the technical aspects of cyber risks. This was because the reports were often signed off by boards and written by staff from outside of IT departments, meaning that there was a limited understanding of the technicalities. There were reputational and security concerns about being too descriptive with their cyber security and being perceived as not in line with peers, or appearing weak.
“We’ve got an accreditation that we gained from Cyber Essentials - the audit and report have to be done as part of that process.” Large business
However, there were instances where cyber security was detailed more thoroughly in corporate reports. One business interviewed aimed their reporting at shareholders, so it was vitally important to go into depth on cyber security to assure them investments were being protected. Aspects of cyber security covered included innovations in the previous year, any new deployments, and training initiatives. They also detailed the number of threats identified in the course of the last twelve months. This was written by cyber security staff, but simplified and edited by the communications department.
4.2 Cyber security strategies
This year we asked organisations for the first time if they had a cyber security strategy, defined as a document that underpins all policies and processes relating to cyber security. We asked follow up questions to better understand the process used to create their cyber strategy, and the approach to cyber security that it outlines. As Figure 4.4 shows, fewer than a quarter of businesses (23%) or charities (19%) have a formal cyber security strategy in place.
Figure 4.4: Organisations that have a formal cyber security strategy
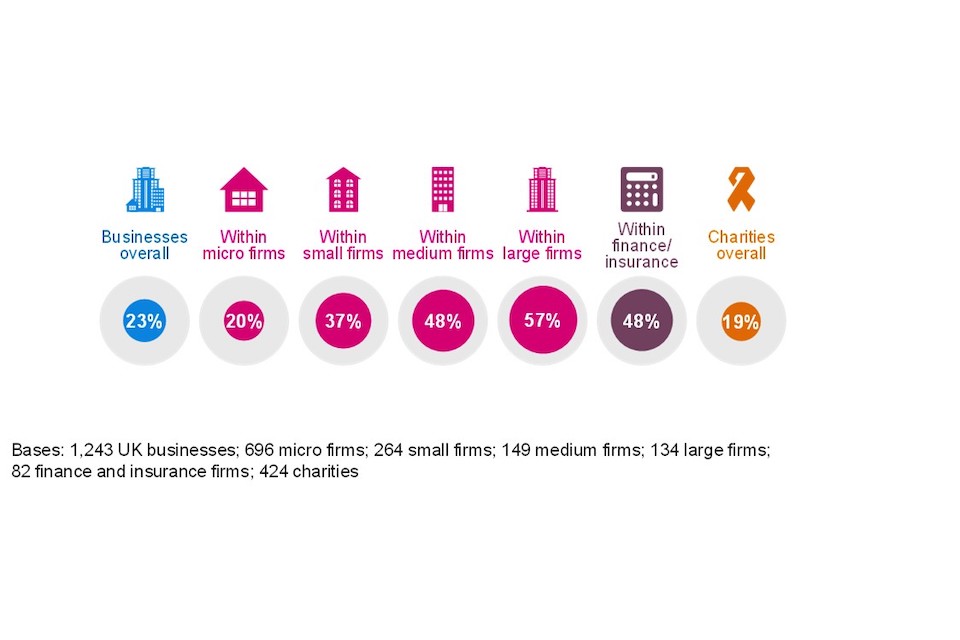
This figure rises to almost half (48%) of medium sized business and is almost six in ten (57%) amongst large businesses. Whilst effective sample sizes are small, cyber security strategies are more often put in place by financial and insurance firms (48%). Among the very largest charities with an income of £5 million or more (41%) the proportion with a formal cyber security strategy is double the charity average (19%).
Among those organisations that do have a cyber security strategy in place, over seven in ten report that this has been reviewed by senior executives / trustees within the last 12 months. This is true of both business (79%) and charities (74%).
Where relevant, five in ten businesses (51%) and four in ten charities (41%) have had their cyber security strategy reviewed by a third party, such as IT or cyber security consultants, or external auditors. This is true of half the micro/small firms (50%) that have a formal cyber security strategy in place, rising to around two-thirds of medium (65%) and large businesses (68%). For businesses that have reviewed their cyber strategy, this is usually part of a wider review (58%) instead of a specific cyber security review (37%). This suggests that cyber security is often perceived or treated as just one area of risk management.
4.3 Insurance against cyber security breaches
Which organisations are insured?
Over four in ten businesses (43%) and almost three in ten charities (27%) report being insured against cyber security risks in some way. These figures are virtually unchanged since 2021 (43% and 29% respectively). The overall figure of 43% in this year’s survey is a clear increase on the 32% in 2020 when the question was introduced, however as only 5 percentage points of the 43 are for a specific cyber security insurance policy this shows that businesses are opting to increase the scope of their current insurance, rather than more proactively seeking cyber cover through an independent insurance policy.
As was the case in 2021 and as Figure 4.5 shows, across all size bands, cyber security insurance is more likely to be through a broader policy, rather than one that is cyber specific. Specific policies are more prevalent among medium (21%) and large firms (28%).
It is worth noting the high level of uncertainty that remains at this question. Among those responsible for cyber security in the private sector, one-fifth (20%) do not know if their employer has any form of cyber security insurance. In charities, this increases to over one-quarter (27%).
Figure 4.5: Percentage of organisations that have the following types of insurance against cyber security risks
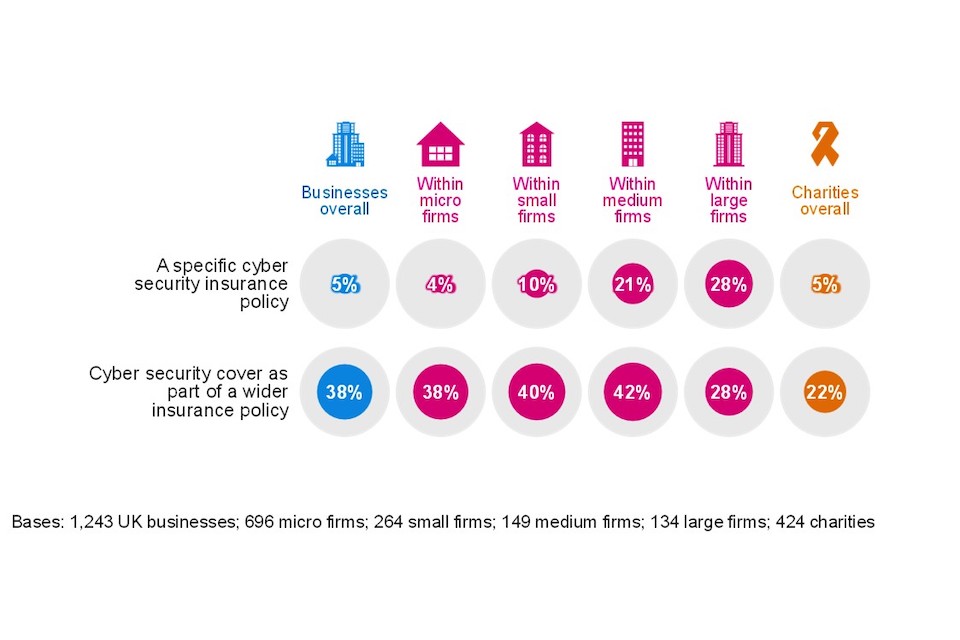
As might be expected, insurance cover is more prevalent in the finance and insurance sector itself. Six in ten finance and insurance firms have some sort of coverage against cyber security breaches (60%, vs. 43% overall). Even here, this is not a specific cyber security insurance policy in most cases (only 23% of these firms have a specific policy). Other sectors where over half reported some form of cyber insurance were:
- Professional, scientific, and technical firms (55%)
- retail or wholesale (51%)
Higher-income charities (with £500,000 or more) are more likely than others to have cyber security cover (57%), either as part of a general insurance policy (41% vs. 22% overall) or within a specific policy (16% vs. 5% overall). This becomes a much larger majority among the very high-income charities (70%). Each of these figures is virtually unchanged since 2021.
Making an insurance claim
Of those with some form of cyber insurance, a tiny proportion of businesses and charities report having made an insurance claim to date. It is less than one percent among businesses and two percent of those charities with cyber security insurance in place.
In 2021 seven percent of large businesses with a relevant policy said they had made a claim under their cyber security insurance. This year not a single large business reported making a claim.
Why organisations have cyber insurance and what’s in policies
As in previous years, we asked organisations about their cyber insurance policies. There were a number of reasons that explained why organisations took out insurance and what was in their policies:
- Insurance providers’ expertise on breach recovery was a key reason for taking out a cyber insurance policy. This was to ensure continuity in the event of a disruptive breach. Some policies gave access to legal help and expertise, as well as a forensic analysis of what caused the breach. Insurers were also able to help organisations recover their systems in the event of a breach. Compensation for damages was also mentioned as a benefit to insurance during breach recovery, but this was largely assumed, so did not tend to influence when choosing a policy.
- Expertise on threat management was another key part of a cyber insurance policy. Some insurance providers provided organisations with services on threat monitoring and management. For instance, one organisation stated that their insurance gave them the ability to monitor the dark web and to flag if any of their accounts were being sold on it.
- Insurance policies helped organisations build a cyber security framework, often in order to become accredited. Some organisations took out insurance because it was necessary to comply with accreditations such as Cyber Essentials or ISO 27001.For those who did not fully comply with accreditations, the checklist insurance companies demanded to be eligible for a policy acted as a framework to ensure good cyber hygiene.
- In previous years organisations have mentioned protection against ransomware and assistance with payments as a key reason for getting insurance. However, this year it was mentioned that this had become more difficult with insurance companies raising premiums or not being able to cover ransoms at all.
“Legal cover in particular [is key]. And being able to bring in a digital forensic team that is really skilled with enough manpower to deal quickly and efficiently with the incident. Our international security team - they don’t have infinite resources, they’re not sufficiently expert in digital forensics, especially at short notice.”
Large business
4.4 Technical cyber security controls
Each year, the survey has asked whether organisations have a range of technical rules and controls in place to help minimise the risk of cyber security breaches. The full list is shown in Figure 4.6. Many of these are basic good practice controls taken from government guidance such as the 10 Steps to Cyber Security or the requirements of Cyber Essentials. Towards the end of this chapter, we map survey responses to these schemes to estimate how many organisations are operating in line with the guidance.
Almost every business (96%) and nine in ten charities (87%) has at least one rule or control in place and as Figure 4.6 indicates, a clear majority have a broad range of basic rules and controls in place. The most frequently deployed rules or controls involve malware protection (83% of business and 68% of charities), password policies (75% and 57%), network firewalls (74% and 56%) and restricted IT administration rights (72% and 68%). Seven in ten businesses (71%) and just over half of charities (53%) also back up data securely via a cloud service.
By contrast, monitoring user activity (33% and 32%), providing separate Wi-Fi networks for staff and visitors (33% and 26%) and the use of virtual private networks (32% and 26%) are less frequently used by either businesses or charities.
The biggest difference between businesses and charities in terms of their rules for cyber security is the use of personally owned devices (56% vs 30%). This can be seen most clearly looking at the smaller charities with <£100,000 income where only 24% have this rule; these charities are often heavily reliant on donations to keep operating and so may not be able to provide staff with basic IT equipment such as a work mobile or laptop and so using a personal device is necessary.
Backing up of data is also extremely common among businesses – nine in ten (87%) have backups either on cloud servers or elsewhere – again this is less common among charities (74%). Having fallen to 68% last year, this specific result for charities is now approaching the figure recorded in 2020 (77%).
There are two elements of cyber security to which businesses and charities appear to afford the same level of importance. Business and charities are equally likely to have specific rules for storing and moving personal data (both 49%); and monitoring of user activity (33% and 32%).
Two-factor authentication was covered for the first time in this year’s survey. Just over a third of businesses (37%) and just under a third of charities (31%), have a requirement for their people to use two-factor authentication when accessing their network, or for applications they use. This is more common among medium (64%) and large (79%) businesses and within high-income charities (67% of those with £500,000 or more). Two-factor authentication is noticeably more prevalent among businesses in information and communications (63%). Conversely, fewer than one in five (18%) businesses operating within the food and hospitality sector employ two-factor authentication procedures. It is also relatively under deployed among utilities, production, and manufacturing businesses (28%).
Figure 4.6: Percentage of organisations that have the following rules or controls in place
| Rules or controls | Businesses | Charities |
|---|---|---|
| Up-to-date malware protection | 83% | 68% |
| A password policy that ensures that users set strong passwords | 75% | 57% |
| Firewalls that cover the entire IT network, as well as individual devices | 74% | 56% |
| Restricting IT admin and access rights to specific users | 72% | 68% |
| Backing up data securely via a cloud service | 71% | 53% |
| Security controls on company-owned devices (e.g. laptops) | 61% | 45% |
| An agreed process for staff to follow with fraudulent emails or websites^ | 57% | 40% |
| Backing up data securely via other means | 56% | 50% |
| Only allowing access via company-owned devices# | 56% | 30% |
| Rules for storing and moving personal data securely | 49% | 49% |
| A policy to apply software security updates within 14 days | 39% | 23% |
| Any requirement for two-factor authentication* | 37% | 31% |
| Monitoring of user activity | 33% | 32% |
| Separate Wi-Fi networks for staff and visitors^ | 33% | 26% |
| A virtual private network, or VPN, for staff connecting remotely* | 32% | 26% |
Bases: 1,243 UK businesses, 424 charities; # Only asked of Half B 593 UK businesses, 250 charities; ^ Only asked of Half A, 658 UK businesses, 185 charities *New codes added for 2022
As in 2021, businesses in three sectors are consistently among the least likely to have many of these rules or controls in place:
- the food and hospitality sector;
- the construction sector;
- entertainment, services and membership organisations.
As highlighted in Chapter 3, those in food and hospitality were the least likely to give cyber security a high priority (66% vs. 82% of all businesses) and had among the lowest incidence of a board member being assigned this role (25%). Consequently, in addition to having the lowest adoption of two-factor authentication, food and hospitality firms are less likely than others to report having up-to-date malware protection (68%, vs. 83% overall), password policies (64% vs. 76%) or network firewalls in place (54%, vs. 76% overall).
Trends over time
Comparing the deployment of the various controls and procedures to the 2021 survey, most figures are in line with a year ago. This is true for both businesses and charities. There are some notable exceptions though, as follows:
- fewer business said they only allow access via company-owned devices (down 7 percentage points from 64% to 56%)
- more charities report backing up data securely via other means (up 10 points from 40% to 50%);
- more charities also report using a virtual private network or VPN for staff connecting remotely (up 6 points from 20% to 26%);
- despite this relative strengthening of charities’ activities, in all three cases the figure remains below that for businesses.
These changes, or rather the relatively small number of them, represent a more stable picture for business than last year, and suggest the steady improvements previously observed among charities might be reactivated. In last year’s report it was noted how qualitative research suggested the 2021 data could have reflected the general upheaval caused by the COVID-19 pandemic. As more organisations had to pivot to allow home working, the feedback from the qualitative strand suggested this made it harder for organisations to centrally implement and manage technical controls covering all their users. The lack of change could indicate organisations have either been unable to return to standard practices pre-pandemic or have adapted to a less proactive way of approaching cyber security.
4.5 Staff training and awareness raising
This survey does not explore cyber security skills and training in detail, given that there is another annual DCMS study dealing with this topic – the UK cyber security labour market series – the latest of which was published in 2021. Nevertheless, this is an important aspect of the 10 Steps guidance so, we have recorded the proportion of organisations that have undertaken training or awareness raising activities around cyber security in the past year.
Our results (Figure 4.7) suggest that in the 12 months prior to the survey just under one in five businesses (17%) and charities (19%) provided training or awareness raising sessions specifically for those not directly involved in cyber security. These figures are similar to last year (14% and 18% respectively). As they did in 2021, the figures are aligned with the DCMS labour market study, although we record slightly higher proportions offering staff training in this area (10% of businesses and 12% of charities did so in the labour market study).
In both the labour market study and this Cyber Security Breaches Survey, relevant training and awareness raising sessions are more commonplace in larger organisations. Over six in ten large firms (61%) and charities with an income of £5million or more (64%) said they have offered this training in the past 12 months. In both micro/small businesses and charities with an income below £100k the figure is 16%.
Figure 4.7: Percentage of organisations that have had training or awareness raising sessions on cyber security in the last 12 months
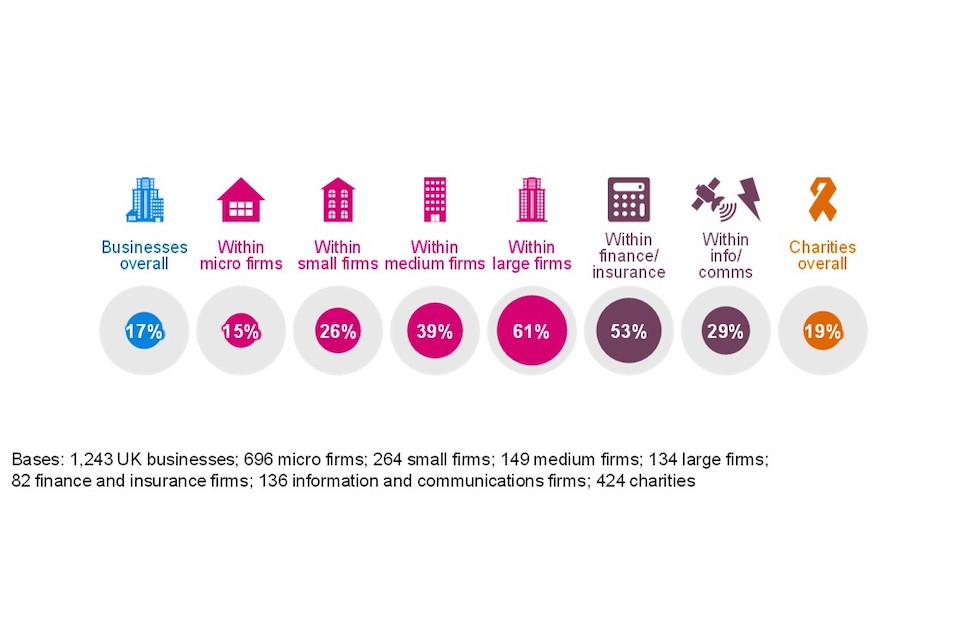
The proportion of finance and insurance businesses offering cyber security training to staff has risen from 39% to 53% since last year. Along with information and communications (currently 29%) it remains the business sector most likely to use training or awareness raising sessions to improve staff understanding of cyber security.
Last year we reported that in many sectors fewer than one in ten businesses were offering staff cyber security guidance. These included entertainment, service and membership organisations, construction, utilities and production and retail and wholesale. Now at least 11% in every sector report having carried out cyber security training or awareness raising sessions in the past 12 months. Within entertainment, service and membership organisations, and retail and wholesale almost one in five firms are now taking such initiatives (both 19%).
Culture of good practice around cyber security
Despite the low proportion of organisations undertaking cyber security training in Figure 4.7, organisations felt they tended to have a good staff culture around security and vigilance. This was even the case of good cyber security practice was implicit or accidental. There was a strong focus on protecting data within the organisation and the overall security or continuity of the business. This was particularly apparent for those that dealt with personal data.
“GDPR and confidentiality are absolutely central to our work… we’re trying to catch up with ourselves about it, but we’re very conscious about keeping info safe. It’s embedded in our policies.”
Small charity
That being said, there were significant challenges in trying to explicitly change or improve cyber security. Staff were often resistant to change if they felt it made it more difficult to do the core activities of their role. Therefore, the messaging needed to be managed carefully. Organisations able to embed culture successfully did so by communicating change well.
There was constant and consistent dialogue between cyber and IT teams (in the case of larger organisations), key decision makers and the wider body of staff. This allowed for a consensus to be built and meant that they were implemented gradually. The language used in any communications was also important. Information from specialist staff needed to be tailored, so that end users would understand why the change was important in improving security and what it involved for them. Ultimately there needed to be a balance between not placing too much burden on employees, whilst still being able to implement necessary changes.
When it came to initiatives to embed change, organisations were better able to implement cyber security changes as part of a wider programme to increase business resilience or efficiency. This was because the organisation’s board or senior leaders were able to drive the change as opposed to IT staff having to lead it. Therefore, the wider body of staff were better able to understand their role in any changes and it was easier to get buy-in throughout the organisation.
For more gradual change and reminders of best practice a multi-pronged approach was favoured. This involved communications via email, mock phishing exercises, conversations with specialist staff and informal and formal training. This kept staff interested in and alert to cyber threats. It also ensured as many staff as possible showed vigilant behaviour towards a wide range of cyber threats. This was tailored to staff level and role. More junior staff tended to have initiatives focused on individual behaviours and senior staff were informed about the strategic risk a poor cyber security culture posed.
“I send out little warnings and bits of info fairly regularly. Only in little bitesize chunks as majority of workforce are young and really not interested. I target it to the person.”
Large charity
4.6 Responsibility for cyber security
We recorded the job titles of those who completed the survey interview, who were identified by their organisation as being most responsible for cyber security. This provides an insight as to the likely seniority and influence of these individuals.
However, we need to exercise caution when interpreting these results – they do not necessarily show the definitive proportion of organisations that have a Chief Information Officer (CIO) or Chief Information Security Officer (CISO), for example. In these organisations, we may have been directed to another senior individual with more day-to-day responsibility for cyber security, such as a senior IT colleague.
- Generally, the larger the business the more specific the job title or function of the person covering cyber security matters. In micro businesses with fewer than 10 employees, it is most likely to be the Chief Executive (22%), business owner (19%), or another in a senior but general non-IT role (18%). Fewer than one in ten micro businesses have someone specifically in an IT role looking after cyber security matters (5%).
- In small businesses, general office managers (19%), those with another senior management role (15%), or finance directors/controllers (12%) tend to take on cyber security responsibilities.
- Only in medium and large businesses, does the responsibility tend to be taken by those with a specific IT remit or within an IT department. For example, most large businesses have an IT director or equivalent (34%) or an IT manager/ technician / administrator (19%), looking after their cyber security. The respective figures for medium sized businesses are 17 and 21 percent.
- The pattern of results, and differences by size, is relatively similar across charities. In a quarter of cases (24%), a trustee performs this function, although this drops to just five per cent among high-income charities (with £500,000 or more). Within the very largest charities (with income of £5 million or more) almost four in ten (38%) interviews were completed by an IT Director or equivalent. This is very similar to the proportion among large businesses (34%).
4.7 Outsourcing of cyber security functions
Around four in ten businesses (39%) and just over three in ten charities (31%) have an external cyber security provider. These figures are consistent with those recorded in the previous two surveys (2021, 2020). As Figure 4.8 shows, outsourcing of cyber security tends to increase substantially among non-micro businesses. The same is true for high-income charities, with six in ten (58% of those with £500,000 or more) saying they outsource.
Figure 4.8: Percentage of organisations that have an external cyber security provider
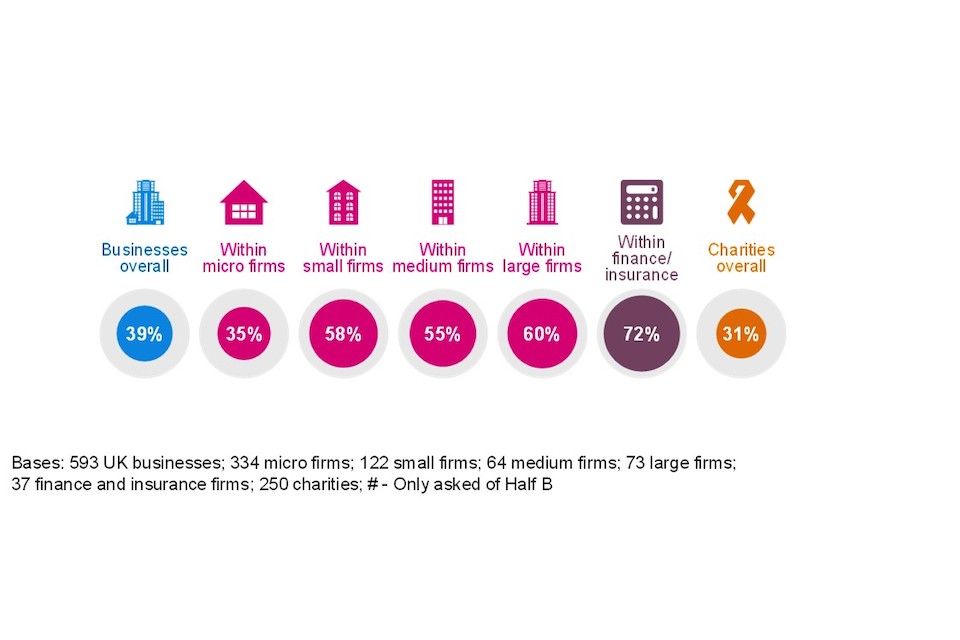
Presumably because they tend to have adequate and specialised internal resources, fewer than three in ten (27%) information and communications businesses utilise external cyber security providers. Among financial and insurance firms the figure is over seven in ten (72%).
4.8 Cyber security policies and other documentation
Do organisations formally document their approaches?
The survey has asked whether organisations have formal cyber security policies in place several years in a row. From 2018 to 2020, this increased from 27% to 38% across businesses, but last year dropped to 33%. A similar pattern was seen among charities.
This year the proportion of businesses with formal policies in place covering cyber security risks stands at 36 percent, so similar to that seen in 2020, but not a significant increase on 2021. The corresponding figure for charities has also remained consistent at 35%. However, the overall data masks some large differences and movements by business size. Large and medium sized businesses remain more likely than small or micro firms to have cyber security policies in place, but among the larger enterprises their prevalence appears to be falling.
In 2021 three-quarters (75%) of medium sized business had cyber security policies. This was three times higher than among micro business (27%). There remains a large gap, but in 2022 the proportion among medium-sized businesses fell nine percentage points to 66%, while among micro business it rose five points to 32%. Hence, the proportion is now two, rather than three times higher among medium sized business.
When looking at business continuity plans, significantly more micro businesses have plans that cover cyber security than in 2021 (32% vs. 26% last year). However, within both small and medium sized enterprises the figure is seven points lower than in 2021, meaning the overall figure is at a similar level. A majority of high-income charities (54%) have a business continuity plan that explicitly covers cyber security.
Figure 4.9: Percentage of organisations that have the following kinds of documentation
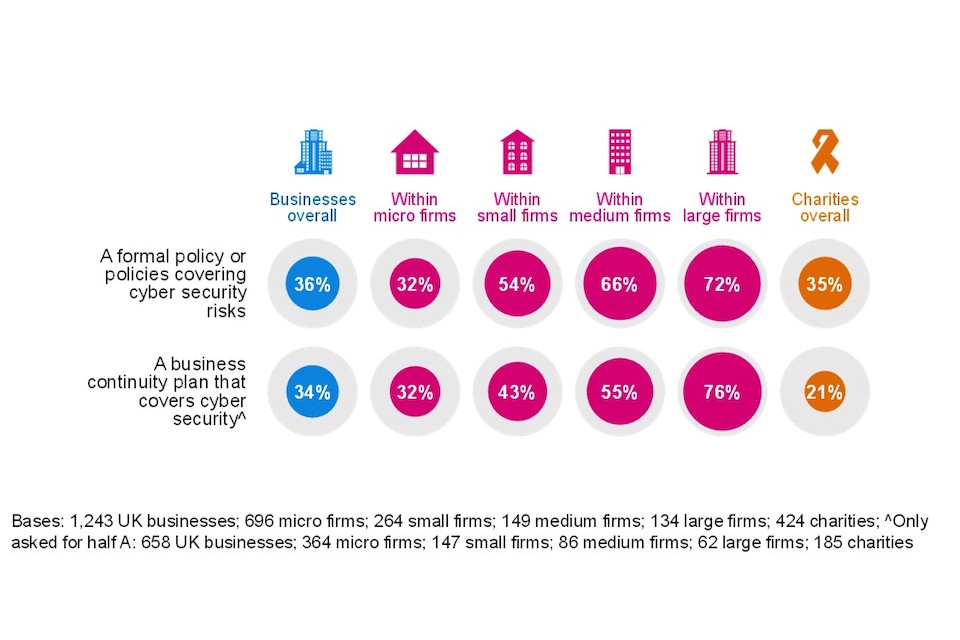
More than any other, it is the finance and insurance sector that ensures it has formal cyber security policies and continuity plans in place. Around two-thirds (65%) have the former and three-quarters (72%) the latter. Both figures are very similar to those recorded in 2021.
After finance and insurance, those engaged in information and communications are relatively more likely to have formal policies (54%) or continuity plans (49%) in place. Just over half (55%) in the health, social care and social work sector have formal policies, and a similar proportion (51%) in the professional, scientific, and technical sector have drawn up continuity plans that cover cyber security.
When were policies last reviewed?
Of the 36% of businesses and 35% of charities that have cyber security policies in place, over four in ten (44% and 47% respectively) reviewed these policies within the last six months (Figure 4.10). For businesses the figure is similar to last year (42%), but still below the last pre-pandemic survey where 52% had reviewed policies or documentation in the past six months.
When looking at the proportions undertaking a review of policies at least annually, the figure for business (73%) is below that recorded last year (82%). By contrast, among charities the proportion reviewing within the past 12 months (79%) is similar to last year (76%). As mentioned above, it appears that businesses have not reverted to pre-pandemic activities and instead have adapted their approach post-pandemic. They have not been able to prioritise reviews of their cyber security documentation now two years on from the profound changes to people’s working arrangements and increased external threats.
Figure 4.10: When organisations last created, updated, or reviewed their cyber security policies or documentation
| Organisation | In the last 3 months | 3 to under 6 months ago | 6 to under 12 months ago | 12 to under 24 months ago | 24 months ago or earlier | Don’t know |
|---|---|---|---|---|---|---|
| Businesses | 25% | 19% | 29% | 14% | 5% | 8% |
| Charities | 21% | 26% | 32% | 11% | 4% | 6% |
What is covered in cyber security policies?
Where they have policies, organisations tend to cover a wide range of cyber security considerations. Nine in ten businesses (90%) and charities (90%) with formal cyber security policies said these ‘procedures’ covered at least one of the eight aspects included in our survey question.
The aspects most often covered by policies are data storage and the appropriate use of IT devices. As illustrated in Figure 4.11, these feature within the cyber security policies of at least seven in ten business and charities with such documentation. Three-quarters (76%) of charities’ policies also cover remote or mobile working, a figure above that for businesses (61%). Charities are also more likely than businesses to report that their cyber security policies cover what can be stored on removable devices such as USB sticks (69% vs 56%) or the use of personally owned devices (63% vs. 51%).
Figure 4.11: Percentage of organisations with cyber security policies that have the following features in their cyber security policies
| Features of cyber security policy | Businesses | Charities |
|---|---|---|
| How data is supposed to be stored | 76% | 75% |
| What staff are permitted to do on organisation’s IT devices | 72% | 72% |
| Remote or mobile working | 61% | 76% |
| What can be stored on removable devices (e.g. USB sticks) | 56% | 69% |
| Use of cloud computing | 56% | 56% |
| Use of network-connected devices | 56% | 58% |
| Use of personally-owned devices for business activities | 51% | 63% |
| Use of Software as a Service | 34% | 33% |
Bases: 605 businesses with cyber security policies; 197 charities
Results are similar to 2021. This shows businesses prioritised continuity over cyber security in the aftermath of the pandemic and survey results shows that cyber security policies have not been reprioritised since.
The frequency of all eight cyber security policy areas within organisations with cyber security policies faced a decline against the previous year. A few areas had noticeable reductions, such as remote or mobile working (down 9 percentage points), what can be stored on removable devices (down 9), cloud computing (down 8) and smart devices (down 7). Among charities the proportion with cyber security policies that cover data storage dropped 10 percentage points (from 85% to 75%). In contrast the charities’ figure for remote or mobile working increased 10 percentage points (from 66% to 76%).
Up to now cloud computing had increasingly been covered in businesses’ cyber security policies – 52% in 2016, 60% in 2020, and 64% in 2021 - but this has now fallen back to 56%.
4.9 Cyber accreditations and government initiatives
This section looks at both government and external cyber accreditations and initiatives. It looks at which organisations adhere to specific accreditations. It then combines some of the individual results covered earlier in this chapter, to provide estimates showing how many businesses and charities are fulfilling the range of requirements laid out in two government initiatives: Cyber Essentials and the 10 Steps to Cyber Security.
Cyber Essentials
The government-endorsed Cyber Essentials scheme enables organisations to be independently certified for having met a good-practice standard in cyber security. Specifically, it requires them to enact basic technical controls across five areas:
- boundary firewalls and internet gateways
- secure configurations
- user access controls
- malware protection
- patch management (i.e., applying software updates).
Chapter 3 highlighted that there is an overall low awareness of Cyber Essentials among both the business (16%) and charity (19%) populations. A higher proportion of organisations do have technical controls in these five areas, but this has declined amongst businesses since last year.
Our survey maps the five areas to individual questions. In total, 24% of businesses (vs. 29% in 2021) and 17% of charities report having technical controls in all five areas.[footnote 6] As might be expected, this is considerably higher for medium businesses (46%) and large businesses (59%). The charities with very high incomes are closest to large businesses (62% of those with incomes of £5 million or more have all these controls).
In a separate question, we also asked organisations if they recognise adhering to either the Cyber Essentials or Cyber Essentials Plus standards. Both ask organisations to implement cyber security measures in the same areas, but the latter includes an external technical assessment. As in 2021 only a small minority of businesses (6% vs. 4% in 2021) and charities (6% vs. 4%) report adhering to Cyber Essentials and just 1% of businesses and 2% of charities say they have the Cyber Essentials Plus standard. Among large businesses, this rises to 35% for Cyber Essentials and 17% for Cyber Essentials Plus.
Other accreditations
We also asked organisations if they adhere to any of the following standards or accreditations:
- ISO 27001 – an international standard for an Information Security Management System
- The Payment Card Industry Data Security Standard (PCI DSS)
- Any National Institute of Standards and Technology (NIST) standards
Of these, the PCI DSS standard is the most widespread, with a third of businesses (32%) adhering to this. Almost half (49%) of medium sized firms now say they adhere to this standard. Fewer than one in ten (8%) businesses adhere to ISO 27001 (rising to 23% of large businesses), while 4% of businesses adhere to any NIST standards (20% of large businesses). In summary, with the exception of PCI DSS, it is only among large business that we see more than one in five enterprises adhering to external standards.
Overall, one in five charities (19%) now follow PCI DSS. Among charities with a very high income almost six in ten (57%) say they use the PCI DSS standard, while two in ten (19%) adhere to ISO 27001.
Reflecting the higher propensity to take online payments in certain sectors, there are some notable differences in the use of PCI DSS across different activities. A majority of food and hospitality businesses (61%), entertainment, service, or membership organisations (56%), and retail and wholesale businesses (53%) adhere to PCI DSS. This is compared to the average figure of 32%. Almost one in five (17%) businesses within health and social care adhere to ISO27001, compared to the average of eight per cent.
Figure 4.12: Percentage of organisations adhering to various cyber security standards or accreditations
| Cyber security accreditations | Businesses | Charities |
|---|---|---|
| The Payment Card Industry Data Security Standard (PCI DSS)^ | 32% | 19% |
| ISO 27001# | 8% | 4% |
| Cyber Essentials | 6% | 6% |
| National Institute of Standards and Technology Standards# | 4% | 6% |
| Cyber Essentials Plus | 1% | 2% |
Bases: 1,243, 658, 593 UK businesses; 424, 185, 250 charities; ^ Only asked of Half A, 658 UK businesses; 185 charities; # Only asked of Half B, 593 UK businesses, 250 charities
Overall adherence to cyber security standards appears to be similar to that reported for 2021. The only exception is an increase in the proportion of charities that now use the PCI DSS standard, up from 11% to 19%.
Challenges surrounding cyber security accreditations
In the qualitative interviews, we discussed take-up of different cyber security standards and accreditations with participants, including the ISO27001 and the Cyber Essentials Standard and the Cyber Essentials Framework. Businesses, charities, and educational institutions tended to adhere to a standard because they needed it for a particular contract, such as a contract with the government. However, some organisations adhered to a particular standard because they felt their customers would want them to, and others were motivated by GDPR concerns. Organisations tended to feel that adhering to these standards improved their knowledge of cyber security. It was common across all sizes of organisation that they felt standards were not flexible enough for them, however, there were issues with adhering to standards and accreditations which did vary between small and large organisations.
Small organisations
The requirements of certain standards were considered to be too stringent by some smaller organisations. Some of the small organisations we spoke to tried to align themselves with the ISO27001 but were not technically approved by it. For some, this was due to the cost of an audit that was required for full compliance, which was too great for the smallest organisations to bear. Others said that the stringency of the requirements were difficult for small organisations to comply with, due to the fact that many would not have a cyber security or IT team to help them. The smallest organisations tended to feel when standards were designed, it was with larger organisations in mind.
“If you are following ISO27001, there are certain things you are supposed to do and not do in terms of segregation of concerns…being a small company of 3 people, that’s incredibly difficult. Not everybody having admin roles…is a key principle, and that’s quite tricky when there’s only 3 of you” Small business
Large organisations also faced challenges around implementing standards and accreditations. Although small organisations had challenges due to a smaller number of employees, larger organisations tended to struggle because of the larger number of service users. For example, a university cyber security coordinator that we spoke to felt that it was particularly challenging for them to properly adhere to cyber security standards due to the large number of service users using personal devices. In larger organisations, it is harder to ensure that all service users are using systems in a safe way. This makes it difficult to ensure that all standards are being adhered to.
“The first time we did the Cyber Essentials it took us a few hours to think over how we would do things differently, but now we would pass it as a matter of course.”
Large business
10 Steps to Cyber Security
The 10 steps to cyber security is a piece of government guidance that breaks down the task of protecting an organisation into 10 key components. It is intended to provide an acceptable level of cyber hygiene to mitigate against the majority of attacks. It is not, however, an expectation that organisations fully apply all the 10 Steps – this will depend on each organisation’s ways of working.
This year NCSC updated their 10 steps guidance,[footnote 7] which are detailed below. We have not mapped the figures onto the previous year’s findings due to these changes.
These steps have been mapped to several specific questions in the survey (in Table 4.1), bringing together findings that have been individually covered across the rest of this chapter. This is not a perfect mapping – many of the steps are overlapping and require organisations to undertake action in the same areas – but it gives an indication of whether organisations have taken relevant actions on each step.
Table 4.1: Percentage of organisations undertaking action in each of the 10 Steps areas
| Step description – and how derived from the survey | Businesses | Charities |
|---|---|---|
| Risk management – Organisations who update boards at least annually and have at least 2 of the following: a cyber security policy or strategy, adherence to Cyber Essentials or Cyber Essentials Plus, undertake risk assessments, have cyber insurance (either a specific or non-specific policy), undertake cyber security vulnerability audits, have an incident response plan, managing suppliers or supply chain cyber risks. | 41% | 36% |
| Engagement and training – Organisations that train staff or do mock phishing exercises | 29% | 25% |
| Asset management – Organisations that list of critical assets | 28% | 29% |
| Architecture and configuration – Organisations that configure firewalls and either: secure configurations, i.e., security controls on company devices or have a policy around what staff are permitted to do on company devices | 54% | 38% |
| Vulnerability management – Organisations that have a patching policy and at least one of the following: undertake vulnerability audits, penetration testing, update anti-malware, or have a policy covering SaaS | 37% | 23% |
| Identity and access management – Organisations that restrict admin rights or password policy or two factor authentication | 87% | 77% |
| Data security – Organisations with cloud or other backups and at least one of the following: secure personal data transfers, have policy covering removable storage or on how to store data | 53% | 48% |
| Logging and monitoring – Organisations with monitoring tools or if log breaches and had a breach | 44% | 37% |
| Incident management – Organisation with incident response plans or formal debriefs | 69% | 71% |
| Supply chain security – Organisations that monitor risks from suppliers or wider supply chain | 14% | 10% |
The vast majority of businesses (93%) and charities (89%) have undertaken at least one of the ten steps. Half of businesses (49%) and four in ten charities (39%) have taken action on five or more of the 10 Steps, as Figure 4.13 shows. Large businesses are the only organisation type in the survey for which any sizeable proportion take action to identify and mediate potential cyber security risks that arise through their supply chain. For example, only 12% and 4% of micro businesses and charities take action to address supply chain cyber risks, giving cause for concern as smaller organisations compose a high proportion of the UK population and are often more reliant on outsourced IT providers.
Figure 4.13: Percentage of organisations that have undertaken action in half or all the 10 Steps guidance areas
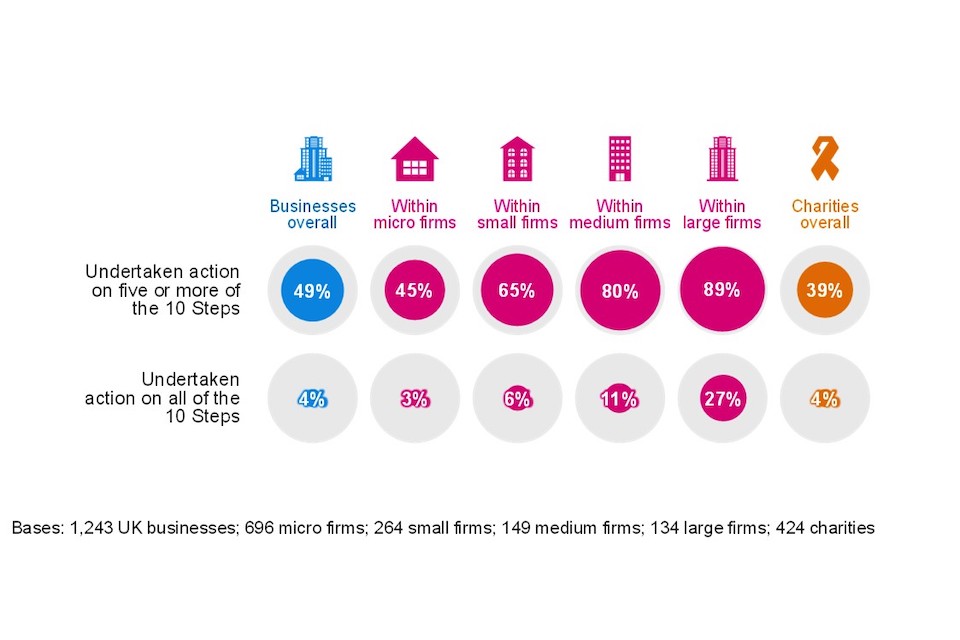
Chapter 5: Incidence and impact of breaches or attacks
This chapter explores the nature, extent and impact of cyber attacks and other cyber security breaches on organisations over the past year. We also provide broad estimates of the financial cost of these breaches and attacks.
Across these findings, the survey aims to account for all the types of breaches or attacks that organisations might face. This includes accidental breaches, as well as ones perpetrated intentionally. It also includes recorded cyber attacks that did not necessarily get past an organisation’s defences (but attempted to do so). We do, nevertheless, isolate and discuss the cases that had a material outcome, such as a loss of money, assets or other data.
It is important to remember that the survey can only measure the breaches or attacks that organisations have themselves identified. There are likely to be hidden attacks, and others that go unidentified, so the findings reported here may underestimate the full extent of the problem.
Note on comparability to previous years
The findings across this chapter are not comparable with those from the 2016 survey, where the initial question on breaches as asked as a yes or no question. This meant there have been due to significant changes in the types of breaches or attacks being recorded from 2017 onwards.
In 2021, we substantially changed the way we capture the cost of cyber security breaches within the survey, in order to get more accurate estimates. Therefore, we do not make direct comparisons from before 2021, but do comment on the broad pattern of the data in relation to previous years. The changes are summarised in section 5.5.
5.1 Identified breaches or attacks
Around four in ten businesses (39%) and a three in ten charities (30%) report having any kind of cyber security breach or attack in the last 12 months (Figure 5.1). We calculate these percentages by merging together the proportions that identified any of the different types of breaches or attacks mentioned in the survey (listed in Figure 5.2).
Larger businesses are more likely to identify breaches or attacks than smaller ones – this has been a consistent pattern in each year of the survey. High-income charities (62% of those with £500,000 or more) and three-quarters with very high incomes (76% of those with £5 million or more) were significantly more likely to record any breaches or attacks.
Figure 5.1: Percentage of organisations that have identified breaches or attacks in the last 12 months
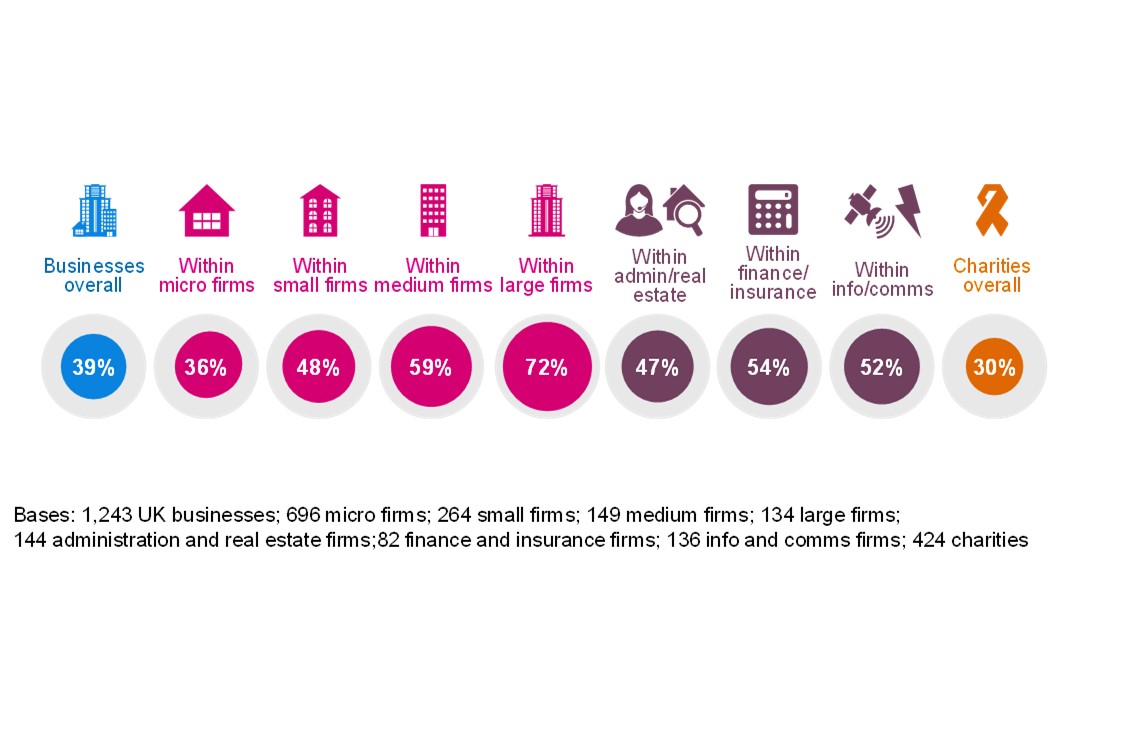
Finance and insurance firms, and information and communications firms are more likely than average to have identified breaches or attacks, which is consistent with previous years.
Types of breaches or attacks identified
Figure 5.2 shows the types of breaches and attacks that organisations report having, among those that have identified any in the last 12 months. The most common by far is phishing – staff receiving fraudulent emails or being directed to fraudulent websites. This is followed, to a much lesser extent, by impersonation others impersonating organisations in emails or online and then viruses or other malware .
One of the consistent lessons across this series of surveys has been the importance of staff vigilance, given that most cyber actors use social engineering techniques to gain access to the target organisation’s networks.
At the same time, among the organisations identifying any breaches or attacks, just over half (51% of businesses and 54% of charities) say they have only experienced phishing attacks and no other kinds of breaches or attacks. This falls to one in five large businesses (20%) one quarter of medium businesses (23%). In this sense, cyber security is always not a one-dimensional issue for organisations.
Figure 5.2: Percentage that have identified the following types of breaches or attacks in the last 12 months, among the organisations that have identified any breaches or attacks
| Which of the following breaches or attacks has your organisation identified in the last 12 months? | Businesses | Charities |
|---|---|---|
| Phishing attacks | 83% | 87% |
| Other impersonating organisation in emails or online | 27% | 26% |
| Viruses, spyware or malware (excluding ransomware) | 12% | 11% |
| Denial of service attacks | 10% | 2% |
| Hacking or attempted hacking of online bank accounts | 8% | 6% |
| Takeover of organisation’s or users’ accounts | 8% | 6% |
| Ransomware | 4% | 4% |
| Unauthorised accessing of files or networks by outsiders | 2% | 2% |
| Unauthorised listening into video conferences or instant messages | 1% | 3% |
| Unauthorised accessing of files or networks by staff | 1% | 1% |
| Any other breaches or attacks | 3% | 3% |
Bases: 573 businesses that identified a breach or attack in the last 12 months; 180 charities
This broad pattern is similar across size bands and sectors. However, medium and large businesses that have identified any breaches or attacks are more likely to report a wider range of types. For example, they are more likely to pick three or more categories from Figure 5.2 (31%, vs. 13% of businesses overall ). Specifically, they are more likely to report:
• Phishing attacks (94% of medium/large firms, vs. 83% overall); and • impersonation (63%, vs. 27% overall).
Large firms specifically were more likely to report unauthorised use of computers or networks by staff (13%, vs. 1% overall).
The top three types of attacks have remained consistent since 2017 (i.e., since the question was first asked in this form), in line with Figure 5.2. However, the pattern of responses is now very different from the 2017 survey, but has remained consistent since 2020. This indicates that the evolution of the types of breaches that organisations have been facing has now become a more settled threat landscape. Changes from 2017 to 2022 include:
• a rise in phishing attacks (from 72% to 83%) • a fall in viruses or other malware (from 33% to 12%) • a fall in ransomware (from 17% to 4%).
The proportions of attack types have remained consistent since the 2020 survey, which gives us a good level of confidence in these outputs, while also highlighting the prevalence of social engineering.
Trends over time
The proportion of businesses and charities reporting any breaches or attacks has remained similar to last year. However, this contradicts the longer term trend for both organisation type. There has been a decline in the proportion of businesses identifying breaches or attacks since 2017 (39% vs. 46%). Conversely, there has been a significant increase for charities since we started surveying them in 2018 (30% vs. 19%).
Figure 5.3: Percentage of organisations over time identifying any breaches or attacks
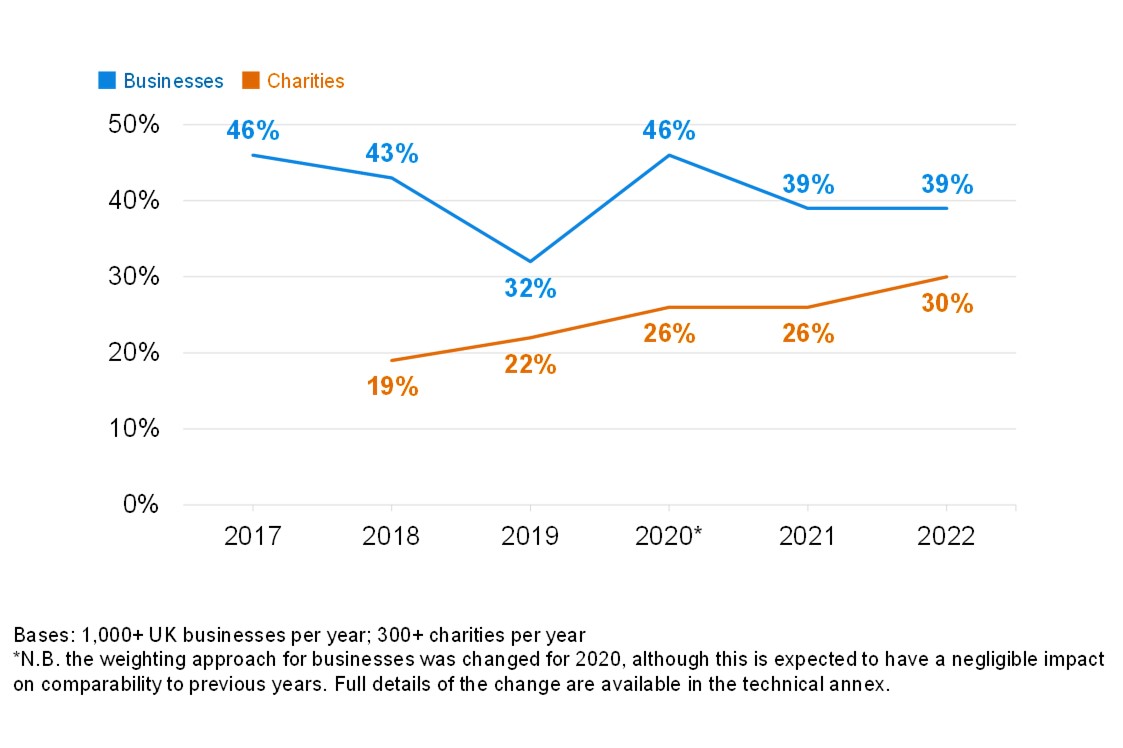
As discussed in last year’s report there were a range of possible reasons for the long-term decline in reporting cyber-attacks amongst businesses. Internally there has been no recovery in the decline in defensive behaviours seen last year. The lower proportion of businesses deploying technical controls and the challenges in monitoring employees could be a permanent adaptation to the vast economic changes seen in the last 24 months. Therefore, businesses are now less capable of identifying breaches than they were two years ago. However, that is not to say this has been driven entirely by internal factors. Changes in attacker behaviour may have made it more difficult for businesses to identify breaches.
5.2 The breaches and attacks considered most disruptive
Among the organisations that report having had breaches or attacks in the past 12 months, phishing attacks are most commonly considered the most disruptive types of attack that organisations face (by 63% of these businesses and 70% of these charities ). This is unsurprising, given that around half of these businesses and charities only recall experiencing phishing attacks and not any other kinds of cyber security breaches.
It is therefore worth looking specifically at the organisations that report any other breaches in addition to phishing attacks, and what these organisations consider to be the most disruptive types of breaches or attacks they have faced. Figure 5.4 shows that, even among this group, phishing attacks are still considered as being the most disruptive to the business, but impersonation attacks are just as disruptive for businesses.
Figure 5.4: Percentage that report the following types of breaches or attacks as the most disruptive, excluding the organisations that have only identified phishing attacks in the last 12 months[footnote 8]
| Which of the following breaches or attacks were the most disruptive (excluding those organisations which only identified phishing attacks) in the last 12 months? | Businesses | Charities |
|---|---|---|
| Phishing attacks | 25% | 36% |
| Other impersonating organisation in emails or online | 25% | 20% |
| Viruses, spyware or malware | 9% | 11% |
| Hacking or attempted hacking of online bank accounts | 9% | 10% |
| Takeover of organisation’s or users’ accounts | 8% | 6% |
| Denial of service attacks | 8% | 0% |
Bases: 333 businesses that identified a breach or attack, aside from a phishing attack, in the last 12 months; 99 charities.
5.3 Frequency of breaches or attacks
Among those identifying any breaches or attacks, around half of businesses (49%) and almost half of charities (44%) say this happens once a month or more often and around three in ten businesses (31%) and a quarter of charities (26%) say they experience breaches or attacks at least once a week. The overall pattern of the frequency, shown in Figure 5.5, is similar to 2021.
Figure 5.5: How often organisations have reported breaches or attacks in the last 12 months
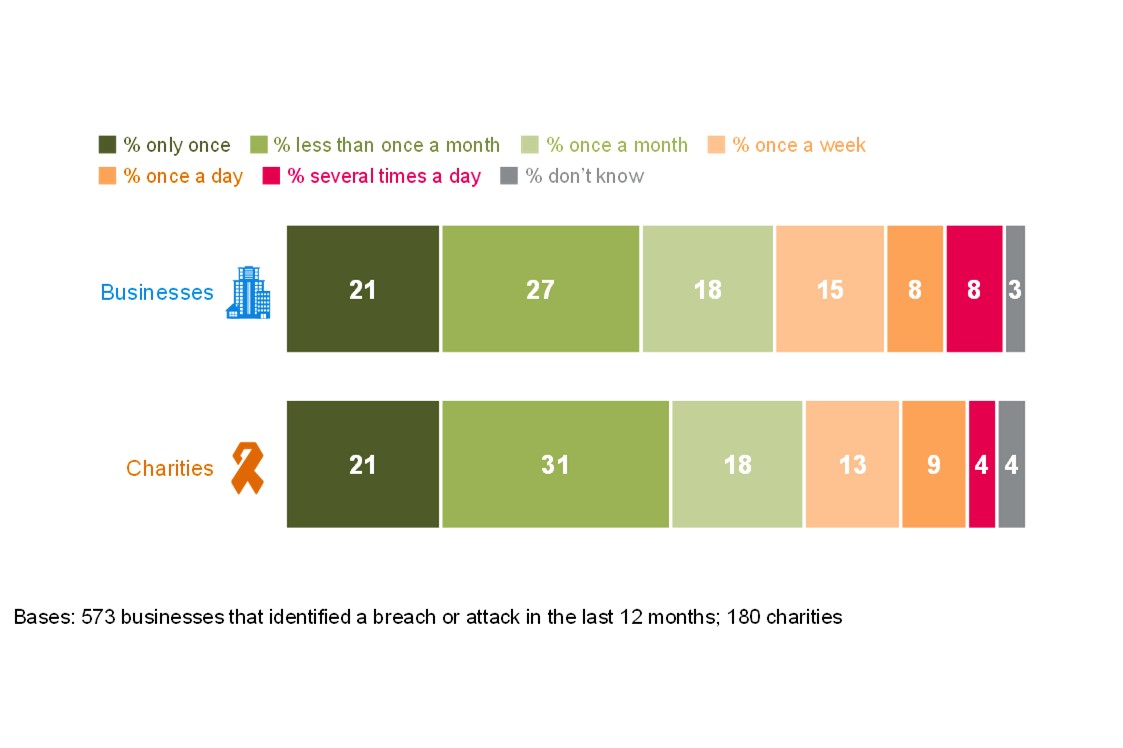
Looking at the longer-term trend, it remains the case that fewer businesses and charities are reporting breaches or attacks as one-off events over the course of a year than before:
- In 2017, 37% of the businesses identifying breaches or attacks could only recall one instance in the previous 12 months. This is now 21%, similar to what was reported in 2021.
- For charities there has been a decline every year. In 2018 (when we first started surveying this group) 36% said they only recalled experiencing a single breach over the year, compared with 21% now.
5.4 How are businesses affected?
Outcomes of breaches or attacks
As Figure 5.6 illustrates, among the 39% of businesses that identify breaches or attacks, only one in five experience a negative outcome, such as a loss of money or data. Among the 30% of charities identifying breaches or attacks, a similar proportion (19%) have these kinds of negative outcomes.
Temporary loss of access to files or networks, disruption to websites, applications or online services and software or systems being corrupted or damaged are the most commonly reported outcomes – although, as Figure 5.6 indicates, organisations can experience a very wide array of outcomes.
A permanent loss of data is much less common, which might be expected given that 87% of businesses and 74% of charities back up their data in some way (see Chapter 4).
As in previous years, organisations that face non-phishing breaches or attacks, for example viruses or ransomware, account takeovers, hacking attempts or other unauthorised access, are much more likely than average to experience a negative outcome as a result (38% vs. 20% overall for businesses and 35% vs. 19% overall for charities). This means that while these kinds of breaches are rarer, the damage they can inflict on organisations is often more substantial. They still, therefore, represent a significant threat for all organisations to consider, alongside more common threats like phishing emails.
Figure 5.6: Percentage that had any of the following outcomes, among the organisations that have identified breaches or attacks in the last 12 months
| Percentage that had any of the following outcomes among the organisations that have identified breaches or attacks in the last 12 months? | Businesses | Charities |
|---|---|---|
| Any listed outcome | 20% | 19% |
| Website or online services taken down or made slower | 7% | 5% |
| Temporary loss of access to files or networks | 6% | 9% |
| Software or systems corrupted or damaged | 5% | 5% |
| Compromised accounts or systems used for illicit purposes | 5% | 4% |
| Lost access to relied-on third party services | 5% | 2% |
| Money was stolen | 3% | 5% |
| Physical devices or equipment were damaged or corrupted | 3% | 3% |
| Lost or stolen assets, trade secrets or intellectual property | 1% | 2% |
| Personal data altered, destroyed or taken | 1% | 2% |
| Permanent loss of files (not personal data) | 1% | 1% |
| Money was paid as a ransom | 1% | 0% |
Bases: 573 businesses that identified a breach or attack in the last 12 months; 180 charities.
These outcomes are all more prevalent among large businesses. Among those that have identified any breaches or attacks, 34% of large businesses had some sort of negative outcome from these (vs. 20% overall).
Nature of the impact
Even breaches that do not result in negative financial consequences or data loss can still have an impact on organisations. One-third of businesses (35%) and almost four in ten charities (38%) that have had breaches or attacks report being impacted in one of the ways noted in Figure 5.7.
Most commonly, breaches or attacks lead to organisations having to take up new measures to prevent or protect against future cases, or staff resources being redirected to deal with the breach. Like with negative outcomes, organisations that report breaches other than phishing are more likely to report an impact from a breach (53% vs. 35% overall for businesses and 57% vs. 38% overall for charities).
Figure 5.7: Percentage that were impacted in any of the following ways, among the organisations that have identified breaches or attacks in the last 12 months
| Percentage that were impacted in any of the following ways, among the organisations that have identified breaches or attacks in the last 12 months? | Businesses | Charities |
|---|---|---|
| Any listed impact | 35% | 38% |
| New measures needed for future attacks | 25% | 25% |
| Added staff time to deal with breach or inform others | 22% | 23% |
| Stopped staff carrying out daily work | 13% | 11% |
| Other repair or recovery costs | 8% | 4% |
| Prevented provision of goods and services | 6% | 4% |
| Loss of revenue or share value | 5% | 2% |
| Complaints from customers | 4% | 6% |
| Reputational damage | 4% | 4% |
| Discouraged you from carrying out a future business activity | 3% | 0% |
| Goodwill compensation or discounts given to customers | 1% | 0% |
| Fines or legal costs | 1% | 0% |
As in previous years, the impact is most substantial for large businesses – for example, 46% of large businesses say they have had to take up new measures to prevent or protect against future cases (vs. 25% of all businesses facing breaches or attacks) and 50% say they needed extra staff time to deal with breaches (vs. 22% overall).
Time taken to recover from the most disruptive breach or attack
The vast majority of businesses (89%) and charities (87%) restore operations from their most disruptive breach or attack within 24 hours. Furthermore , seven in ten businesses (70%) and charities (72%) say it took no time at all to recover, shown in Figure 5.8.
However, for businesses that report breaches or attacks with a material outcome in terms of a loss of money or data (as discussed at the start of this section), the situation is different. In these cases, four in ten (38%) businesses take a day or more to recover (vs. 11% of businesses having any kinds of breaches or attacks, including those without outcomes). There is a broadly similar pattern in the charities data, although the sample of charities that report breaches or outcomes is too small to report here.
Figure 5.8: How long it took organisations to restore operations back to normal after their most disruptive breach or attack was identified
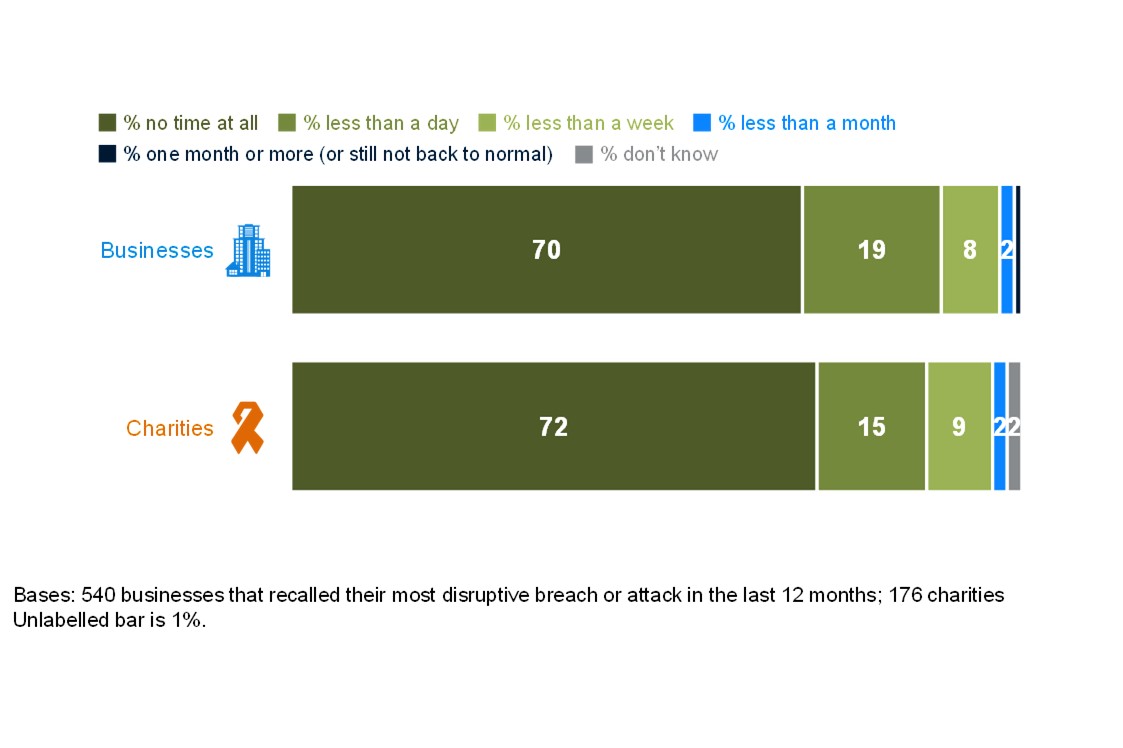
Trends over time
This year’s findings indicate the ability businesses have to mitigate against the effects of cyber attacks have levelled off. As Figure 5.9 shows, the trend for businesses taking no time to recover, and outcomes and impacts of attacked remaining consistent for two years consecutively. From 2017 to 2020 there had been change towards improved ability to absorb negative consequences.
The trends in Figure 5.9 are not due to breaches or attacks becoming less frequent. As covered earlier in this chapter, there has been no notable change in frequency this year.
The survey cannot definitively say what has caused the lack of change. This could be because the legacy of GDPR is now embedded meaning businesses no longer make wholesale improvements to their security. The qualitative research found numerous further barriers to this. This included a lack of board engagement and expertise in larger businesses, low technical knowledge and competing priorities in smaller businesses, with all businesses suffering budgetary constraints.
Figure 5.9: Percentage of businesses over time that have been affected by breaches or attacks in the following ways, among those that have identified any breaches or attacks in the last 12 months
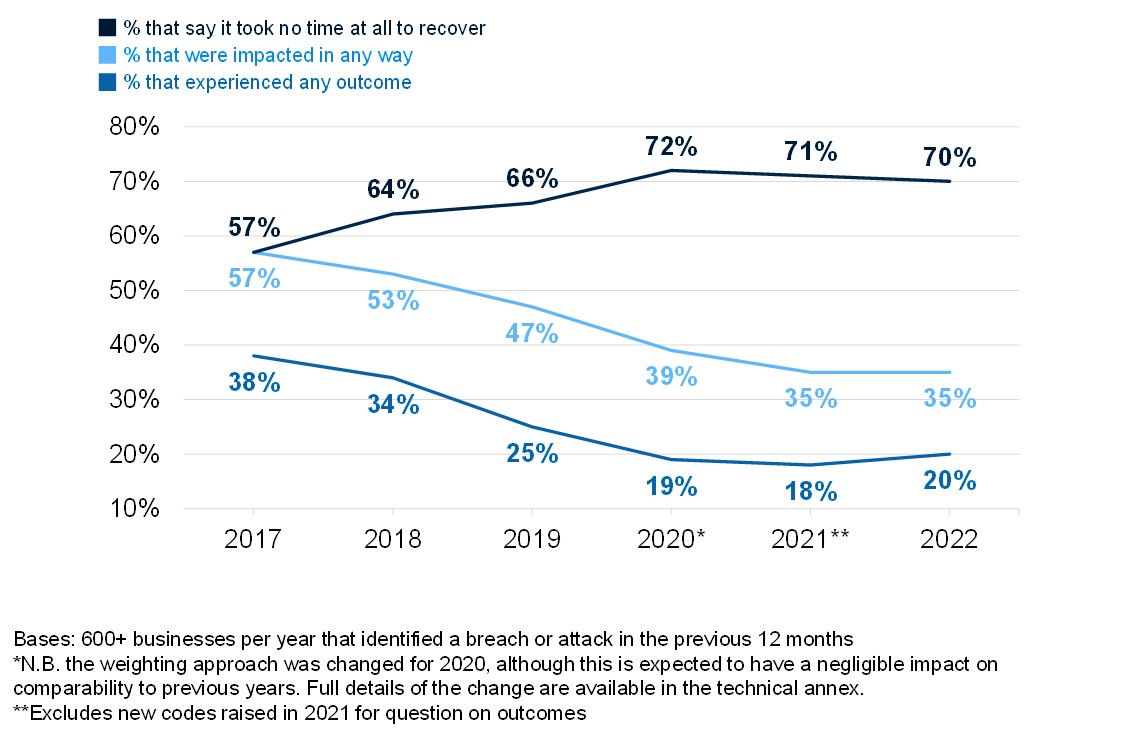
This stabilisation is also observed with charities. A similar proportion of charities this year report breaches or attacks impacting them when compared to last year, but this is fewer than in 2020 (38% vs. 40% in 2021 and 56% in 2020). Like with businesses, the causes are unclear, but there are implications from the qualitative research. Low budgets amongst charities, a lack of board engagement in larger charities and lack of expertise in smaller ones could mean resilience has plateaued.
5.5 Financial cost of breaches or attacks
Each year, this survey series has attempted to capture the cost of cyber security breaches or attacks on organisations. This includes an overarching question covering the cost of all breaches or attacks faced in the last 12 months, and more granular questions breaking down different aspects of the cost of the single most disruptive breach or attack that organisations recall facing in this period.
This year, we made significant changes to the wording and ordering of these questions in the survey, in order to improve the accuracy of the data. These improvements included:
• Redesigning the granular cost questions to follow the cost mapping laid out in a separate 2020 DCMS research study on the full cost of cyber security breaches; • moving the order of the overarching cost question to be after these more granular ones; • allowing respondents to change or revalidate their responses (e.g., after further consultation with colleagues), in a follow-up online survey.
In previous years, while we aimed to be comprehensive in the costs we collected, the questions did not specifically split out direct costs (where there was a transfer of cash involved, like a ransom payment) and indirect costs (like the staff time cost). Some aspects of the cost data in previous years were also more speculative, for example covering long-term costs that might occur in the future. The new questions are more distinct and refined. They avoid organisations making gross oversimplifications or inaccurate guesses with the more speculative aspects or underestimating their costs by omitting a major cost category like staff time.
These changes are substantial, so we cannot make direct comparisons between this year’s data and previous years. We do, however, comment on the broad patterns of the data, for example the differences between smaller and larger businesses, as well as charities.
Overall cost of breaches or attacks
Table 5.1 shows the estimated costs organisations incurred from all the identified breaches or attacks over the past 12 months. When considering the cost, organisations are asked to bear in mind all the potential impacts mentioned in Figure 5.6 .
When filtering down only to breaches with a material outcome, mean costs tend to be higher. We would expect this given that the mean is more susceptible to influence from the higher end of the distribution.
Table 5.1: Average cost of all breaches or attacks identified in the last 12 months[footnote 9]
| - | All businesses | Micro/small businesses | Medium/large businesses | All charities |
|---|---|---|---|---|
| Across organisations identifying any breaches or attacks | ||||
| Mean cost | £1,200 | £861 | £8,040 | £300 |
| Median cost | £0 | £0 | £62 | £0 |
| Base | 550 | 383 | 167 | 173 |
| Only across organisations identifying breaches with an outcome | ||||
| Mean cost | £4,200 | £3,080 | £19,400 | n/a* |
| Median cost | £500 | £500 | £960 | n/a* |
| Base | 129 | 78 | 51 | n/a* |
*Too few charities to analyse.
Costs associated with the most disruptive breaches
Tables 5.2 to 5.5 show cost estimates for the single most disruptive breach that organisations have identified in the last 12 months. Again, these are presented for all breaches, as well as those with an actual outcome, such as a loss of assets or data.
In the survey, we defined short-term direct costs as being any external payments that were made when the breach was being dealt with. This includes, as examples offered to respondents:
- Any payments to external IT consultants or contractors to investigate or fix the problem; and
- any payments to the attackers, or money they stole.
Table 5.2: Average short-term direct cost of most disruptive breach or attack from the last 12 months
| - | All businesses | Micro/small businesses | Medium/large businesses | All charities |
|---|---|---|---|---|
| Across organisations identifying any breaches or attacks | ||||
| Mean cost | £479 | £316 | £4,050 | £35 |
| Median cost | £0 | £0 | £0 | £0 |
| Base | 522 | 368 | 154 | 170 |
| Only across organisations identifying breaches with an outcome | ||||
| Mean cost | £1,650 | £1,332 | £6,490 | n/a* |
| Median cost | £0 | £0 | £0 | n/a* |
| Base | 124 | 76 | 48 | n/a* |
*Too few charities to analyse.
We defined long-term direct costs as external payments in the aftermath of the breach incident.
The examples included in the survey were:
- Any payments to external IT consultants or contractors to run cyber security audits, risk assessments or training
- the cost of new or upgraded software or systems
- recruitment costs if you had to hire someone new, and
- any legal fees, insurance excess, fines, compensation or PR costs related to the incident.
Table 5.3: Average long-term direct cost of most disruptive breach or attack from the last 12 months
| - | All businesses | Micro/small businesses | Medium/large businesses | All charities |
|---|---|---|---|---|
| Across organisations identifying any breaches or attacks | ||||
| Mean cost | £240 | £125 | £2,750 | £36 |
| Median cost | £0 | £0 | £0 | £0 |
| Base | 521 | 368 | 153 | 167 |
| Only across organisations identifying breaches with an outcome | ||||
| Mean cost | £782 | £435 | £6,010 | n/a* |
| Median cost | £0 | £0 | £0 | n/a* |
| Base | 124 | 76 | 48 | n/a* |
*Too few charities to analyse.
We also asked about the costs of any staff time (i.e., indirect costs of the breach). This includes, for instance, how much staff would have got paid for the time they spent investigating or fixing any problems caused by the breach. We explicitly asked respondents to include the cost of this time regardless of whether this duty was part of the staff member’s job function or not.
Table 5.4: Average staff time cost of the most disruptive breach or attack from the last 12 months
| - | All businesses | Micro/small businesses | Medium/large businesses | All charities |
|---|---|---|---|---|
| Across organisations identifying any breaches or attacks | ||||
| Mean cost | £261 | £151 | £2,640 | £86 |
| Median cost | £0 | £0 | £66 | £0 |
| Base | 520 | 367 | 153 | 166 |
| Only across organisations identifying breaches with an outcome | ||||
| Mean cost | £614 | £477 | £2,600 | n/a* |
| Median cost | £191 | £190 | £378 | n/a* |
| Base | 125 | 76 | 49 | n/a* |
*Too few charities to analyse.
Finally, we asked about other indirect costs related to breaches, including the following areas (offered as examples to respondents):
- The cost of any time when staff could not do their jobs;
- the value of lost files or intellectual property; and
- the cost of any devices or equipment that needed replacing.
Table 5.5: Average indirect cost of the most disruptive breach or attack from the last 12 months
| - | All businesses | Micro/small businesses | Medium/large businesses | All charities |
|---|---|---|---|---|
| Across organisations identifying any breaches or attacks | ||||
| Mean cost | £242 | £200 | £1,150 | £44 |
| Median cost | £0 | £0 | £0 | £0 |
| Base | 536 | 375 | 161 | 176 |
| Only across organisations identifying breaches with an outcome | ||||
| Mean cost | £1,050 | £866 | £3,770 | n/a* |
| Median cost | £0 | £0 | £0 | n/a* |
| Base | 127 | 77 | 50 | n/a* |
Commentary on the financial costs
The following key findings can be gleaned from these cost tables:
- The overall costs reported here (in Table 5.1) are considerably lower than last year. However, they are higher for medium and large businesses
- The immediate direct costs of a cyber security incident (Table 5.2) tend to end up being much higher than the costs in the aftermath of an incident (Table 5.3). This could be because calculating immediate costs (e.g., paying a ransom) is easier to calculate and more tangible that accumulating the more long-term costs in the aftermath. However, this is the direct opposite of what was observed last year, where recency bias was suggested as a possible explanation.
- The 2020 study on the full cost of cyber security breaches showed that organisations find it harder to consider the indirect costs (Tables 5.4 and 5.5). Therefore, this may be another area where organisations are significantly undervaluing the overall cost of breaches and attacks.
- Like last year, businesses tend to identify higher costs than charities on average. This does not necessarily mean that charities face a lower risk – it could be that they tend to have a less comprehensive understanding of the cost implications, so report lower costs.
- The median cost is typically £0 across businesses and charities – also a similar pattern to previous years. This reflects the fact that most breaches or attacks do not have any material outcome (a loss of assets or data), so do not always need a response. By contrast, the typical organisation that has dealt with a negative outcome from breaches or attacks does report non-negligible cost costs (a median cost across the year of £500 for businesses overall, and £960 for larger businesses). Organisations that are breached, but are fortunate enough not to lose data or assets, therefore run the risk of systematically underappreciating the seriousness of cyber security breaches and attacks.
- The cost profile of smaller and larger businesses that experience an outcome from a breach varies considerably. The majority of costs for smaller businesses are reported as immediate direct costs after an incident, with indirect costs seen as another significant outlay. For larger businesses the costs are spread far more evenly. Short- and long-term direct costs do make up the majority of their overall costs, though this could be because they are easier to quantify. When looking at the costs of all businesses experiencing a breach, larger businesses report higher costs across all areas.
Chapter 6: Dealing with breaches or attacks
This chapter explores how well businesses and charities deal with breaches or attacks, including identification, response, reporting and adaptation to prevent future cases.
In the survey, questions on this topic were generally framed in terms of the most disruptive breach or attack an organisation had faced in the last 12 months. As these questions ask how organisations respond to cyber incidents, only the 39% of business and 30% of charities that have identified breaches or attacks are referred to, rather than the full sample. The size and sector subgroups therefore tend to have very small sample sizes. As such, subgroup analysis does not tend to show statistically significant differences and is featured much less in this chapter.
The questions on incident response in the first section are, however, asked of the full sample.
6.1 Incident response
Figure 6.1 shows the actions organisations typically say they take in response to a cyber security incident. Most organisations (93% of businesses and 89% of charities) do report having some sort of formalised incident response process, i.e., doing at least one of the things mentioned here. This is much higher than last year (where 66% of businesses and 59% of charities reported having a formalised incident response) but owing to the addition of codes and the restructuring of the question the findings are not directly comparable.
Approaches to incident response are reasonably comprehensive. Two-thirds of businesses (67%) and charities (65%) say they take at least five of the listed actions in the chart when they experience a cyber security incident. This rises to 90% of medium-sized businesses and 93% or large businesses. Though organisations are taking a number of actions, the most frequently mentioned tend to be more reactive approaches on what to do, such as informing directors or assessing impact. Proactive measures, such as written guidance, is less common.
Figure 6.1: Percentage of organisations that take the following actions, or have these measures in place, for when they experience a cyber security incident
| Percentage of organisations that take the following actions, or have these measures in place, for when they experience a cyber incident | Businesses | Charities |
|---|---|---|
| Inform your directors / trustees /governors of the incident | 84% | 84% |
| Assessment of the scale and impact of the incident | 73% | 73% |
| Keep an internal record of incidents | 68% | 75% |
| Inform a regulator of the incident when required | 68% | 70% |
| Debriefs to log any lessons learnt | 66% | 70% |
| Attempting to identify the source | 62% | 62% |
| Roles or responsibilities assigned to specific individuals during/after the incident | 39% | 38% |
| Written guidance on who to notify | 30% | 32% |
| Inform your cyber insurance provider of the incident | 30% | 19% |
| Guidance around when to report incidents externally, e.g. to regulators or insurers | 29% | 29% |
| A formal incident response plan | 19% | 22% |
| Communications and public engagement plans | 14% | 15% |
| None of these | 7% | 11% |
Bases: 1,243 UK businesses; 424 charities
Formalised and multifaceted incident response processes are much more the norm among larger organisations. A clear majority of large businesses and very high-income charities (with £5 million or more) do all the processes listed in the chart, with the exception of communications and public engagement plans. For example, similarly high proportions of large businesses (70%), and very high-income charities (72%) say they have a formal incident response plan. Communications and public engagement plans are far less widespread than the other actions, even among large businesses (49% have plans of this sort). This is interesting, considering that so many organisations are concerned about the reputational damage of cyber attacks or breaches and being seen to have poor cyber security.
The three sectors where cyber security is more likely to be seen as a higher priority are more likely than average to have specific processes in place. They are:
- Finance and insurance;
- Information and Communications; and
- Health and Social Care.
A majority of firms in the finance and insurance sector have stated they have most facets of a response plan in place. The exceptions are communications and public engagement plans, informing their cyber insurance provider and a formal incident response plan. Along with the sectors mentioned above professional, scientific, and technical firms are more likely to undertake some actions. These are having roles and responsibilities assigned to individuals (49% vs. 39% for businesses), keeping an internal record of incidents (77% vs. 68% for businesses) and informing their insurance provider (39% vs. 30% for businesses).
Ransomware payments
This year we asked organisations whether they have a rule or policy to not pay ransomware payments. Just over half of businesses (56%) and four in ten charities (40%) have such a rule or policy. However, it must be noted that there was a high level of uncertainty, with one in five businesses (19%) and one quarter of charities (27%) stating they did not know.
This was consistent across size bands, but large businesses were less likely to explicitly state they did not have a policy (10% vs. 24% for businesses) and more likely to not know (38% vs. 19% for businesses). However, the proportion of businesses stating they did have a policy was consistent across size bands. Likewise, findings were similar across sectors and amongst charities.
First-hand accounts from organisations which experienced a ransomware attack suggest the presence of a policy in this space is not always effective. When faced with the choice, organisations cited system downtime and loss of sensitive data as reasons to pay the ransom. On the other hand, the risk of reputational damage was a key reason not to pay the ransom.
Qualitative insights on ransomware
Ransomware has become a topic of concern for many organisations due to its prominence in the media and potentially devastating impact. We spoke to organisations about the threat they believed ransomware posed to them, and the protections (or lack of) they had in place against it. We also spoke to organisations who had previously been targeted by attacks, and what changes they had made.
There was variation amongst organisations in how they viewed the threat of ransomware: participants tended to strongly believe that ransomware posed a high risk to their organisation. Due to its prominence, ransomware was seen by some as a useful tool to highlight the risk of any kind of cyber attack. Many organisations cited reports of ransomware in the media making them more aware of the damage it could cause. Some believed that even though the level of damage could be high, the likelihood of getting attacked was low. Organisations that believed that ransomware posed no threat to their organisation, did so because their data was not valuable, or because they had their data backed up or stored in a cloud service.
Of those who had not been attacked by ransomware, organisations tended to have an incident response plan which involved shutting down infected systems and notifying staff and relevant parties. Some intended to notify authorities, although they did not specify which authorities these were. Organisations were very concerned about the damage that a ransomware attack could do to their reputation, which some believed was worse than the cost of the attack itself. Of those who had been attacked, organisations mentioned a notable shift in how the organisation approached cyber security in the aftermath. There was particular emphasis on end-user behaviour.
“We don’t have a specific ransomware policy - it’s something you would assess at the time. It’s not always easy when they’ve got you over the barrel.”
Large business
There was a marked difference between large and small organisations in how they perceived the threat of ransomware. Smaller organisations tended to believe that ransomware did not pose a threat. This was because participants either believed it was unlikely to happen, or that they did not have anything of value. Organisations tended to have an informal plan in place in the event of an attack, which involved shutting down systems and re-booting with backed-up data. Smaller organisations often mentioned speaking to an IT provider for advice in the event of an attack. Some organisations had no plan at all. However, those small organisations which viewed ransomware as a serious threat had a strict plan in place in the event of an attack.
“We wouldn’t pay out; we couldn’t afford to pay out.”
Small business
There was a clear difference in attitudes on whether or not an organisation would pay a ransom or not. Those that had not experienced an attack were extremely likely to say they would not pay under any circumstances. This was due to concerns around reputational damage and confidence that their backup systems and incident management plans would cause minimal disruption. However, there were instances where those that had experienced a ransomware attack had paid a ransom, contrary to their policy. This was because, in reality, the disruption caused immediately impacted the organisation’s continuity, so they paid the ransom to become fully operational as soon as possible. These organisations tended to be smaller with low confidence on cyber security, so would pay the ransom as opposed to recovering systems themselves. They also had a lower risk of reputational damage.
“I imagine that we would always take the line of not paying out unless we couldn’t recover adequately in which case, we might think about paying out but I would be 99% certain that we would recover over 90% of our data without having to pay out a ransom.”
Large business
6.2 External reporting breaches or attacks
External reporting of breaches remains uncommon amongst organisations. Only two-fifths of businesses (40%) and a quarter of charities (25%) reported their most disruptive breach outside their organisation, a similar proportion to last year.
For businesses, many of these cases – as in previous years – simply involve businesses reporting breaches to their external cyber security providers and no one else. When excluding these cases, we find that businesses reported externally only in a third of cases (35%). This has been relatively consistent since the 2017 survey.
The top (unprompted) organisations that businesses tend to report breaches to externally are banks, IT providers, internet service providers, Action Fraud and clients, as Figure 6.2 shows. These findings are largely consistent with previous years, though reports are now made more frequently to the Action Fraud website/helpline than directly to police forces.
There are too few charities in the sample (ones that have reported breaches externally) to analyse in this way.
Figure 6.2: Percentage of organisations that report their most disruptive breach or attack of the last 12 months, excluding those that only report to their outsourced cyber security provider
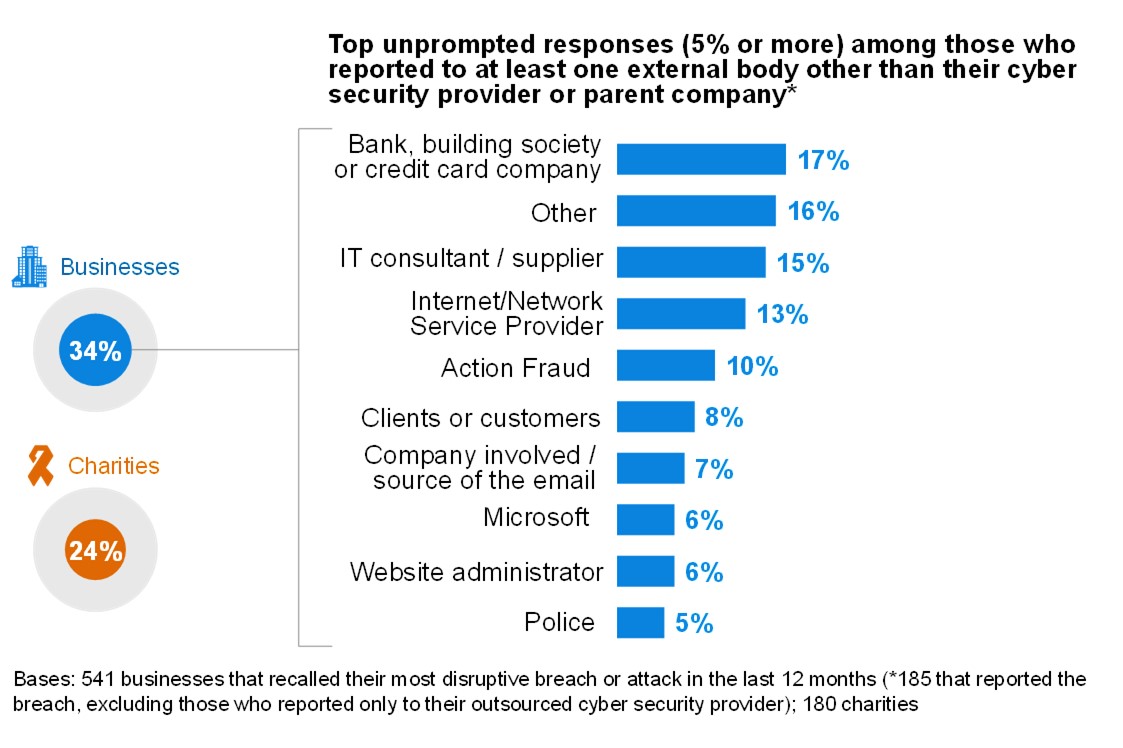
Why organisations report breaches
As Figure 6.2 shows, organisations do not tend to report breaches. The qualitative findings echoed this, with a reluctance from organisations to do any more than they had to do. This sentiment was felt even amongst those who had experienced an attack or even a breach.
When organisations did experience an impactful breach, they reported to who they felt they had to report to. For instance, they would report to the ICO if they were legally obliged to, or to their bank if they lost money via hacking or fraudulent means. Amongst larger organisations, there was also a sense that the reputational risk of not doing so and being caught outweighed the reputational risk of publicising a breach.
“That would be for us for me to assess what happened. Check whether we had to notify the commissioner. If we didn’t have to, we wouldn’t. If we had to, we would, but we’re not going to start shouting from the rooftops that we’ve had a breach, but obviously, if we don’t report it, and it found out that we did, then obviously that’s a big problem, so we follow the rules.”
Large charity
Organisations also saw the benefits in reporting breaches. Firstly, they saw it as a chance to increase knowledge on cyber security internally by learning from external expert help and advice. They also saw, in the sense of the wider economy, that reporting a breach would help aggregate data centrally and reduce the risk of a similar attack happening in the future.
“The benefits of reporting are making sure that all these organisations are aware of potentially new things that are occurring, the volume and the types of attacks, obviously, you know, thinking about it now, it’s probably really, really important for them to be aware of these sorts of things. Particularly if there’s patterns and things occurring across certain sectors.”
Small business
Organisations that did not report breaches tended to say this was because they did not think it was severe enough to warrant external help. There was also a concern amongst larger organisations that they risked their reputation if they did so when the chances were that they would not get found out. However, as detailed above, larger organisations were also motivated to report because they felt they would suffer reputational damage if not.
Smaller organisations did not report breaches because they felt the manpower and cost involved in putting the reports together was not worth it. They also had more immediate priorities both related to the aftermath of a breach and in the running of an organisation. They were also unaware they were required to do so in many instances.
6.3 Actions taken to prevent future breaches or attacks
Among those that have identified any breaches or attacks, around two-thirds of businesses (62%) take action to prevent further breaches, a similar finding to 2021. Significantly fewer charities take action to prevent breaches compared to last year (57% vs. 69% in 2021) .
As Figure 6.3 shows, the most common (unprompted) specific action taken are a mixture of additional staff training or communications, and new technical controls.
Figure 6.3: Percentage of organisations that have done any of the following since their most disruptive breach or attack of the last 12 months
| Percentage of organisations that have done any of the following since their most disruptive breach or attack of the last 12 months | Businesses | Charities |
|---|---|---|
| Additional staff training or communications | 19% | 24% |
| Installed, changed or updated antivirus or anti-malware software | 9% | 6% |
| Changed or updated firewall or system configurations | 9% | 5% |
| Being more careful with emails / blocking / filtering emails | 7% | 4% |
| Other new software or tools (not antivirus or anti-malware) | 5% | 5% |
| No action taken | 36% | 41% |
Bases: 541 businesses that recalled their most disruptive breach or attack in the last 12 months; 176 charities
We can further categorise the answers into changes of a technical nature, people-related changes (e.g. to training or staffing) and governance changes (e.g. updates to policies or other documentation). When viewed in this way, a greater proportion of businesses have made technical changes (33%) compared to people-related changes (24%). In charities, a greater proportion make people related changes (27%), compared with technical changes (23%). For both groups, fewer decided to make changes to their governance processes (8% of businesses and 11% of charities). Charities have taken less action compared to 2021 more generally as opposed to in a specific area, with all of these groups in isolation not experiencing a significant decline.
Medium firms (88%) and large firms (83%) are the most likely to have taken any actions to prevent further breaches or attacks (vs. a 62% average).
As may be expected, the picture in Figure 6.4 changes slightly when looking only at businesses whose most disruptive breach resulted in a material outcome (e.g the loss of files, money, or other assets). More than four in five businesses (83%) took any form of action and are even more likely to focus on technical changes (50%).
Figure 6.4: Percentage of organisations that have done any of the following since their most disruptive breach or attack of the last 12 months, in cases where breaches had material outcomes
There are too few charities in our sample that identified breaches with material outcomes to break down responses at this question.
Chapter 7: Conclusions
This is now the seventh wave of the Cyber Security Breaches Survey. During this time organisations have faced significant challenges and changes to how they work, both in terms of legislation and the wider economy they operate in. We have therefore seen changes in how they view and approach cyber security, as well as how they adapt and react to an evolving threat landscape. This is the seventh publication of the Cyber Security Breaches Survey from 2016 through to 2022, where we look at the cyber security policies and processes of UK organisations, and the cyber threat landscape. Over this time we have seen many changes in how these organisations approach cyber security, as well as how they adapt and react to evolving threats. In last year’s report we concluded with themes arising from Covid-19’s impact on organisational cyber security, while this year we return to a macro view of cyber resilience as firms continue to carry out their everyday operations in the UK cyberspace.
The survey responses are favourable across a number of key components for cyber security:
- Cyber security is now seen as a high priority by a greater proportion of businesses than in any other year of the survey. It has also remained steady amongst charities compared to last year but is significantly higher than the baseline year in 2018. In the qualitative interviews it was found that this was driven by a good high-level understanding at the senior level of the risks cyber attacks pose. This, coupled with the use of board sponsors and cyber security experts enabled organisations to practice good cyber hygiene.
- Organisations have been able to maintain good cyber hygiene, with most rules, policies and controls and risk mitigation techniques remaining steady compared to last year, despite continued challenges. More than 4 in 5 medium and large businesses have taken action for their cyber security in at least 5 areas detailed in the Government guidance; the 10 Steps to Cyber Security. This demonstrates that larger UK enterprises have a good standard of cyber security. Additionally, several technical controls such as access management, malware, firewalls and data security are very commonplace.
- Organisations have been able to implement an engaged culture around cyber security, understanding that staff vigilance is essential to protect against the threat of phishing attacks. In order to ensure staff were on board, communication put out by organisations focused on protecting customers and service users as opposed to any technical details on cyber security. Organisations successfully implementing a good cyber security culture ensure dialogue to staff on cyber security is regular and relatively informal. They strike the right balance between changing initiatives to alter staff behaviour without making it too burdensome and disruptive for employees.
However, there remains to be a lack of both will and skill around organisational cyber security, resulting in gaps in some more fundamental areas of cyber hygiene:
- Organisations take an informal approach to incident management, with fewer than one in five businesses having a formal incident management plan. However, a much greater proportion of organisations have a formal business continuity plan. This demonstrates a clear priority to ensure that business operations continue uninterrupted, while conducting proactive activity into cyber risk management is a secondary consideration. This means there is a focus on maintaining operations in response to serious breach as opposed to proactive cyber risk management.
- Despite cyber security being seen as a high priority area, qualitative research found there is a lack of technical knowhow expertise within smaller organisations and at senior level within larger organisations. This inhibits an organisation’s cyber security for a number of reasons;. These include fostering a tendency to take a reactive approach, viewing investment in cyber security as a cost rather than an investment, being intimidated by terminology and lacking awareness of strategic risks posed to an organisation. Many organisations remain in a reactive approach to cyber security instead of proactively driving improvements.
- There is a clear lack of commercial narrative to effectively negotiate a cyber security budget against other competing organisational priorities. For organisations that do not outsource their IT or cyber security solutions; often the cyber security profile is reliant on the colleague with cyber security responsibilities to communicate and influence board members to drive improvements.
- Additionally, organisations do not tend to engage with industry standards such as Cyber Essentials. Uptake for these is still in the minority. There is a low awareness overall, and those that are aware do not feel accreditations are tailored enough for their needs, meaning they cannot meet criteria.
- Organisations are not publicly disclosing their cyber security profile in their annual reports or otherwise to best inform stakeholders. Qualitative interviews suggested that often annual reports are produced by a colleague in a different department to IT. Additionally, reputational concerns around being negatively compared with peers or perceived as weak led to cyber security being limited in annual reporting to high level risks or strategy, or even omitted entirely.
- There is a theme of organisations opting to outsource their IT solutions to a third party supplier, so as to access the benefits of a larger and more resourced specialist. However, supply chains themselves pose an entry point for attackers and so organisations become only as resilient as their weakest supplier in their supply chain. Fewer than one in ten organisations actively monitor the risks within their supply chain and so this presents a clear risk for the future.
The risk of supply chain attacks remains high, with fewer than one in ten monitoring risks posed by the supply chain. Given cyber security measures vary across businesses it means that businesses that tend to have strong cyber security (e.g., a large finance and insurance firm) are as vulnerable to an attack as their weakest supplier (e.g., a small business in food and accommodation) if they do not monitor their supply chain.
The findings from this year’s survey demonstrate that there is room for improvement in many elements of organisations cyber hygiene. It is clear that cyber resilience is highly influenced by board behaviours. Though the high-level prioritisation of cyber security amongst boards is high, this does not translate into high expertise. Furthermore, cyber and IT staff are unable to justify the business case for cyber security, which impacts ability to make effective cyber security decisions. This means investments are often not made into key areas that enhance organisations’ cyber security. This leads to a reactive approach to cyber incidents as opposed to a proactive approach in limiting cyber risk. This is an area we will closely monitor in future years of the survey.
Last year we stated that it is important for organisations, management boards and IT teams to recognise that good cyber security facilitates better business resilience. The COVID-19 pandemic made this challenging, with many prioritising immediate continuity. This year the findings suggest that organisations have not been able to look at cyber security in this way and improve their overall resilience. Based on what we found in the survey and qualitative interviews there is a role to support organisations in this.
Firstly, guidance and communications could pivot from focusing on the technicalities of implementing cyber controls to how to mitigate against the existential risk cyber security poses to an organisation. This should be written in plain English with the target audience being a senior leader or small business owner with a passing interest in cyber security. Secondly, organisations, particularly smaller ones, stated a preference to informally seek information either through networks or third-party experts. There is an opportunity to use these networks and experts as route to disseminate information, share best practice, and ultimately close the gap between organisations with good and poor cyber hygiene.
Further information
The Department for Digital, Culture, Media and Sport would like to thank the following people for their work in the development and carrying out of the survey and for their work compiling this report.
- Harry Williams, Ipsos MORI
- Eleanor Myers, Ipsos MORI
- Alice Stratton, Ipsos MORI
- Allan Hyde, Ipsos MORI
- Jayesh Navin Shah, Ipsos MORI.
The Cyber Security Breaches Survey was first published in 2016 as a research report, and became an Official Statistic in 2017. The previous reports can be found at https://www.gov.uk/government/collections/cyber-security-breaches-survey. This includes the full report, infographics and the technical and methodological information for each year.
The responsible DCMS analyst for this release is Maddy Ell. The responsible statistician is Robbie Gallucci. For enquiries on this release from an official statistics perspective, please email evidence@dcms.gov.uk.
For general enquiries contact:
Cyber Security Team (4/48)
Department for Digital, Culture, Media and Sport
100 Parliament Street
London
SW1A 2BQ
Telephone: 020 7211 6000
DCMS statisticians can be followed on Twitter via @DCMSinsight.
The Cyber Security Breaches Survey is an official statistics publication and has been produced to the standards set out in the Code of Practice for Official Statistics. Details of the pre-release access arrangements for this dataset have been published alongside this release.
This work was carried out in accordance with the requirements of the international quality standard for Market Research, ISO 20252, and with the Ipsos Terms and Conditions.
Annex A: Guide to statistical reliability
The final data from the survey are based on weighted samples, rather than the entire population of UK businesses or charities. Percentage results are therefore subject to margins of error, which vary with the size of the sample and the percentage figure concerned.
For example, for a question where 50% of the 1,244 businesses sampled in the survey give a particular answer, the chances are 95 in 100 that this result would not vary more or less than 3.4 percentage points from the true figure – the figure that would have been obtained had the entire UK business population responded to the survey. The margins of error that are assumed to apply in this report are given in the following table.[footnote 10]
Margins of error (in percentage points) applicable to percentages at or near these levels
| - | 10% or 90% | 30% or 70% | 50% |
| 1,243 businesses | ±2.1 | ±3.1 | ±3.4 |
| 696 micro firms | ±2.4 | ±3.7 | ±4.0 |
| 264 small firms | ±4.0 | ±6.0 | ±6.6 |
| 148 medium firms | ±5.2 | ±7.9 | ±8.6 |
| 135 large firms | ±5.3 | ±8.1 | ±8.9 |
| 424 charities | ±3.6 | ±5.5 | ±6.0 |
There are also margins of error when looking at subgroup differences. A difference from the average must be of at least a certain size to be statistically significant. The following table is a guide to these margins of error for the subgroups that we have referred to several times across this report.
Differences required (in percentage points) from overall (business or charity) result for significance at or near these percentage levels
| - | 10% or 90% | 30% or 70% | 50% |
| 696 micro firms | ±1.2 | ±1.8 | ±1.9 |
| 264 small firms | ±3.4 | ±5.2 | ±5.6 |
| 149 medium firms | ±4.7 | ±7.2 | ±7.9 |
| 135 large firms | ±4.9 | ±7.5 | ±8.2 |
| 138 high-income charities | ±5.8 | ±8.8 | ±9.6 |
| 82 finance and insurance firms | ±7.2 | ±11.0 | ±12.0 |
Glossary
| term | definition |
|---|---|
| Cyber security | Cyber security includes any processes, practices or technologies that organisations have in place to secure their networks, computers, programs or the data they hold from damage, attack or unauthorised access. |
| Cyber attack | A cyber attack is a malicious and deliberate attempt by an individual or organisation to breach the information system of another individual or organisation. |
| Impact | A negative impact on organisations did not have to involve a material loss. This could be issues relating to staff disruption or implementing new measures in the organisation. |
| Outcome | A negative outcome of an attack involved a material loss from an organisation, such as a loss of money or data. |
| Security breach | A security breach is any incident that results in unauthorised access of data, applications, services, networks and/or devices by bypassing their underlying security mechanisms. |
| Micro business | Businesses with 1 to 9 employees |
| Small business | Businesses with 10 to 49 employees |
| Medium business | Businesses with 50 to 249 employees |
| Large business | Businesses with 250 employees or over |
| Low income charity | Charities with an income of less than £100,000 |
| High income charity | Charities with an income of £500,000 or more |
| Very high income charity | Charities with an income of £5,000,000 or more |
| Cloud computing | Cloud computing uses a network of external servers accessed over the internet, rather than a local server or a personal computer, to store or transfer data. This could be used, for example, to host a website or corporate email accounts, or for storing or transferring data files. |
| Data classification | This refers to how files are classified (e.g. public, internal use, confidential etc). |
| Document Management System | A Document Management System is a piece of software that can store, manage and track files or documents on an organisation’s network. It can help manage things like version control and who has access to specific files or documents. |
| Externally-hosted web services | Externally-hosted web services are services run on a network of external servers and accessed over the internet. This could include, for example, services that host websites or corporate email accounts, or for storing or transferring data files over the internet. |
| Health checks | Health check activities might include things like staff surveys, security assessments or vulnerability scans. Business-as-usual checks would be activities like this that are undertaken no a scheduled basis, e.g. annually. Ad-hoc checks will be the same kinds of activities but just undertaken as a one-off, e.g. in response to an attack. |
| Intellectual property | Intellectual property (IP) refers to the ideas, data or inventions that are owned by an organisation. This could, for example, include literature, music, product designs, logos, names and images created or bought by the organisation. |
| Malware | Malware (short for “malicious software”) is a type of computer program designed to infiltrate and damage computers without the user’s consent (e.g. viruses, worms, Trojan horses etc). |
| Managed Service Provider (MSP) | A supplier that delivers a portfolio of IT services to business customers via ongoing support and active administration, all of which are typically underpinned by a Service Level Agreement. A Managed Service Provider may provide their own Managed Services, or offer their own services in conjunction with other IT providers’ services. |
| Patch management | Having a policy to apply software security updates within 14 days |
| Penetration testing | Penetration testing is where staff or contractors try to breach the cyber security of an organisation on purpose, in order to show where there might be weaknesses in cyber security. |
| Personally-owned devices | Personally-owned devices are things such as smartphones, tablets, home laptops, desktop computers or USB sticks that do not belong to the company, but might be used to carry out business-related activities. |
| Phishing or social engineering | Fraudulent attempts to extract important information, such as passwords, from staff. |
| Ransomware | A type of malicious software designed to block access to a computer system until a sum of money is paid. |
| Removable devices | Removable devices are portable things that can store data, such as USB sticks, CDs, DVDs etc. |
| Restricting IT admin and access rights | Restricting IT admin and access rights is where only certain users are able to make changes to the organisation’s network or computers, for example to download or install software. |
| Risk assessment covering cyber security risks | This is the process of identifying and controlling any cyber security threats to an organisation’s data. |
| Smart devices | Network connected devices, like personal assistants, locks, alarms, or thermostats. |
| Threat intelligence | Threat intelligence is where an organisation may employ a staff member or contractor, or purchase a product to collate information and advice around all the cyber security risks the organisation faces. |
| Two-Factor Authentication | Two-Factor, or Multi-Factor, Authentication is an electronic authentication method in which a user is granted access to a network or application only after successfully presenting two or more pieces of evidence to an authentication mechanism (e.g. a password and a one-time passcode). |
-
On 20 October 2022 DCMS amended the percentage figure for charities who have acted in at least five of the 10 Steps to Cyber Security from 40% to 39% in this section of the text, as an inconsistency in the report was identified. The 39% figure quoted in this section now aligns with the data presented in figure 4.13. ↩
-
Where subgroup mean scores are compared, the large variation in the data often means that these differences are not statistically significant – this is made clear throughout. However, looking at the pattern of mean scores across subgroups, and the direction of travel since the 2016 and 2017 surveys, can still generate valuable insights in these instances. ↩
-
Subgroup differences highlighted are either those that emerge consistently across multiple questions or evidence a particular hypothesis (i.e., not every single statistically significant finding has been commented on). ↩
-
This year we split the sample on certain question codes into two groups, Half A and Half B. Where this has been applied we have made a note in the base text of the relevant figure. ↩
-
These aggregated results (for organisations updating managers at least annually or quarterly) across this section exclude the five per cent of businesses and charities that say they update senior managers each time there is a breach (although these are still included in the base). ↩
-
The charities mentioning their country’s charity regulator are also included in the 10 per cent mentioning a government or public sector information source. ↩
-
This is the percentage of businesses and charities that say they have all the following rules or controls: having network firewalls, security controls on company-owned devices, restricting IT admin and access rights to specific users, up-to-date malware protection, and a policy to apply software updates within 14 days. ↩
-
The ‘Ten Steps to Cyber Security’ government guidance was rewritten this year. Therefore, Ipsos have reconfigured how we map responses in the survey to the Ten Steps, and, as such, they are not comparable to 2021 or previous years ↩
-
We have combined the ransomware and other malware response options from Figure 5.2 for this chart. ↩
-
The cost estimates in this section are presented to three significant figures, or to the nearest whole number (if under 100). The mean and median scores exclude “don’t know” and “refused” responses. They merge together the answers from respondents who gave a numeric value as well as those who gave only a banded value (because they did not know the exact answer). For the latter, we have imputed numeric values from the given banded values. For this overall cost question, we opted to remove two outlier values for businesses from the calculations. We lay out this approach in detail in the Technical Annex ↩
-
In calculating these margins of error, the design effect of the weighting has been taken into account. This lowers the effective base size used in the statistical significance testing. The overall effective base size was 817 for businesses (vs. 901 in 2020) and 267 for charities (vs. 312 in 2020). ↩
